RansomHouse: Stolen Data Market, Influence Operations & Other Tricks Up the Sleeve
Written by Anastasia Sentsova
Executive Summary
- This research aims to identify connections between RansomHouse, and other groups based on the investigation of multiple crossclaims of victims. Emerging after the Babuk source code leak in late 2021, RansomHouse has been linked to multiple groups, including White Rabbit, Mario ESXi, RagnarLocker, and Dark Angels (Dunghill Leak).
- Investigation of the RansomHouse data leak site (DLS) also revealed multiple crossclaims with other groups, indicating potential cooperation. According to the analysis of RansomHouse’s dataset (May 9, 2022, to February 28, 2024) of entities posted on its DLS, 11 out of 73 claimed victims were crossclaimed by other groups.
- Further investigation revealed potential associations of RansomHouse with Alphv/BlackCat, LockBit 3.0, BianLian, and RagnarLocker. Through our findings and corroborated by open-source reporting from other researchers, including the identification of shared emails and a consistent timeline of crossclaims, there is evidence suggesting potential collaboration among these syndicates.
- Snatch and Stormous, singled out in a separate case, were identified as closely cooperating with RansomHouse and/or Dark Angels, engaging in hybrid ransomware/hacktivist activities that blend ransomware with influence operations under the guise of hacktivism. While Dark Angels and RansomHouse primarily function as ransomware groups, Snatch and Stormous align themselves with hacktivists. Observed causes include pro-Palestine and pro-Russia sentiments, with a focus on attacking US and European entities, also involving associated individuals, particularly government officials.
- The analysis of the geopolitical alignment indicates that RansomHouse, Snatch, and Stormous are likely aligned with Russia. This is based on the observed infrastructure analysis revealing connections originating from servers based in Russia and other artifacts. Additionally, an analysis of major pro-Russian media channels reveals strong support for these groups, reinforcing their narratives in a way that aligns with and supports the broader agenda of the Russian state.
- Data sharing among ransomware groups introduces new challenges. Previously stolen data is reused in extortion attempts, creating false impressions of new attacks. The integration of hacktivist-like activities by groups like Snatch and Stormous also underscores the need for enhanced security measures to protect sensitive data and mitigate reputational damage at governmental and individual levels.
Introduction
One of the main aspects of ransomware operations, often determining the success of their extortion efforts, is the utilization of data leak sites. These platforms are crucial in supporting double-extortion tactics, where actors not only encrypt the victim’s data but also threaten to publicly release it unless a ransom is paid.
Recent observations within the realm of Russian-speaking ransomware highlight a notable trend: multiple groups claiming to have breached the same victim. While it is theoretically possible for multiple syndicates to simultaneously target the same victim, the frequency of such cross-claims suggests a higher likelihood of collaboration in data sharing among the actors involved.
The rise of Russian-speaking ransomware has indeed been significant, with its impact extending across former Soviet Union countries where the language is historically spoken. In this report, however, our focus is primarily on groups with geopolitical alignment with Russia. Therefore, to maintain clarity and specificity, we will refer to subjects of our analysis as Russian groups or actors.
In this research, we mainly focused on the RansomHouse group, which drew our attention due to the high number of crossclaims with various other groups compared with the total number of entities posted on their DLS. To uncover RansomHouse’s operations, we delved into the group’s history, tracing its emergence back to May 2021 when the Babuk source code was leaked, giving rise to multiple other syndicates, including RansomHouse.
Through analyzing the patterns and dynamics surrounding these crossclaims between RansomHouse and other groups, we aimed to delve into the extent of collaboration within the Russian ransomware ecosystem. Our analysis suggests significant data-sharing collaborations among multiple groups, with RansomHouse prominently involved. These collaborative efforts also implicate groups like Snatch and Stormous, which engage in hybrid operations blending traditional ransomware activities with what we name as hacktivist-like activities, masking influence operations under this guise.
Identifying data-sharing collaborations among ransomware groups is a significant finding that has important implications for incident response actions. It also underscores the interconnected nature of the Russian ransomware landscape and enhances our understanding of its ecosystem. By recognizing the potential for collaboration, organizations can implement more robust defense measures to mitigate the impact of such attacks and extortion attempts.
Babuk Code Leak & Emergence of RansomHouse
The attribution of RansomHouse and its emergence history, has sparked considerable debate and speculation within the cybersecurity community. Indeed, in an environment where ransomware groups frequently undergo rebranding, attributing attacks to specific groups can be challenging.
The group’s emergence began with the leak of Babuk source code. On September 2, 2021, a prominent member of the Russian-speaking DarkWeb forum XSS operating under the moniker dyadka0220, published the code. Babuk, also referred to as Babyk was first observed approximately at the beginning of 2021. Throughout their operations, Babuk actors targeted numerous high-profile victims, getting away with millions of dollars of ransom payments.
The leak became a Pandora’s box, spawning several new groups, including RansomHouse, and being adopted by existing groups at that time such as Conti and Alphv/BlackCat. The Babuk Locker “builder” became attractive to hackers due to its functionality in targeting ESXi servers, which are widely popular among large corporations and businesses. According to the Cybersecurity and Infrastructure Security Agency (CISA) advisory published on February 8, 2023, 3,800 VMware ESXi servers have been compromised globally.
The backstory behind the leak is also intriguing and provides valuable insights into the Russian ransomware underground. The incident followed an internal dispute between dyadka0220 and boriselcin (aka wazawaka), key members of Babuk. Boriselcin was later identified as Mikhail Matveev and sanctioned by the DOJ, with actions announced on May 13, 2023. Among approximately 65 identified victims, the Metropolitan Police Department in Washington D.C. was one of them, targeted on April 26, 2021.
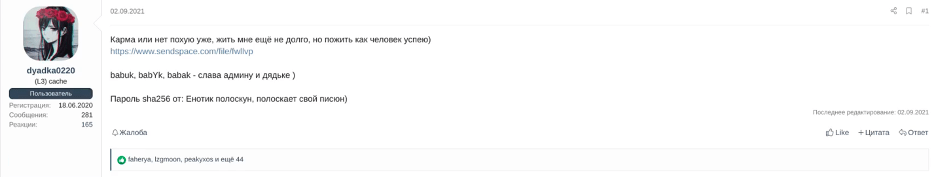
Source: XSS forum
Metropolitan Police became the subject of a dispute between actors, likely occurring sometime in May of 2021 when the Babuk shutdown was announced, eventually leading to a split. On July 11, 2021, Matveev launched a ransomware forum RAMP, first operating under the moniker TetyaSluha, which was soon changed to Orange. Soon after, on August 22, 2021, a new ransomware group named Groove was announced on RAMP, describing itself as “an aggressive financially motivated criminal organization dealing in industrial espionage.”
Four days after the Babuk source code leak, on September 7, 2021, Matveev posted a blog on his Groove data leak site explaining the situation surrounding the group. According to the blog, Matveev claimed that the negotiation failed due to the lack of pressure on the victim and “unprofessionalism” by their affiliate. The actor then decided to end the business relationship with their former colleagues. It was agreed that Matveev would retain Babuk’s DLS domain, where the first RAMP forum was built (eventually, Matveev rebuilt RAMP on a different domain), while their affiliate would keep the source code.
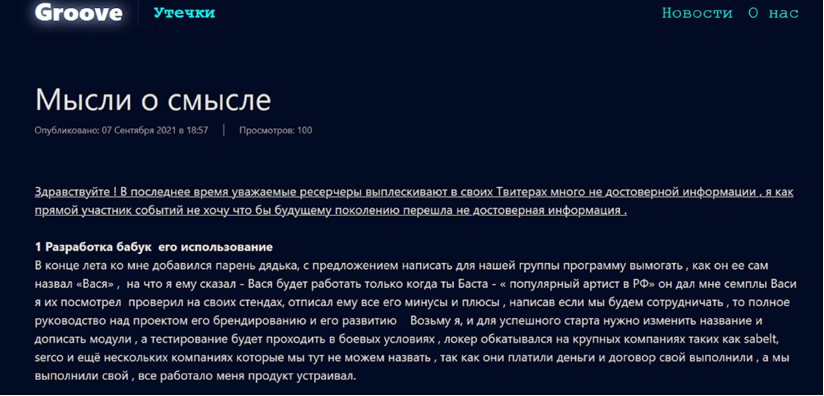
Source: Groove data leak site
These events provide a compelling example of the interconnected nature of the Russian ransomware ecosystem. They also serve as a reminder that the investigation of ransomware involves much more than just the technical aspects, as its landscape is often shaped by various internal and external factors. With constant rebranding and the launching of new groups, the underlying reason in some cases may indeed be as simple as actors being unable to get along with each other.
It is important to highlight that this behavior and interconnectedness between groups are particularly prevalent among Russian actors. This may also explain why Russian ransomware continues to flourish, as well as the success of the Ransomware-as-a-Service (RaaS) business model, wherein an affiliate responsible for a breach can collaborate with numerous other groups. Driven by financial motivation and bolstered by the foundation of established personal relationships – essential in Russian society – the ransomware ecosystem thrives. Mikhail Matveev, for example, was identified as participating across at least three variants: LockBit, Babuk, and Hive.
Such cultural characteristics that foster strong support for close collaboration might also contribute to and explain instances of crossclaims of victims we observed, which is the main focus of our research. But first, let’s take a closer look at the operations of RansomHouse.
RansomHouse: The Beginning – The SLGA Case
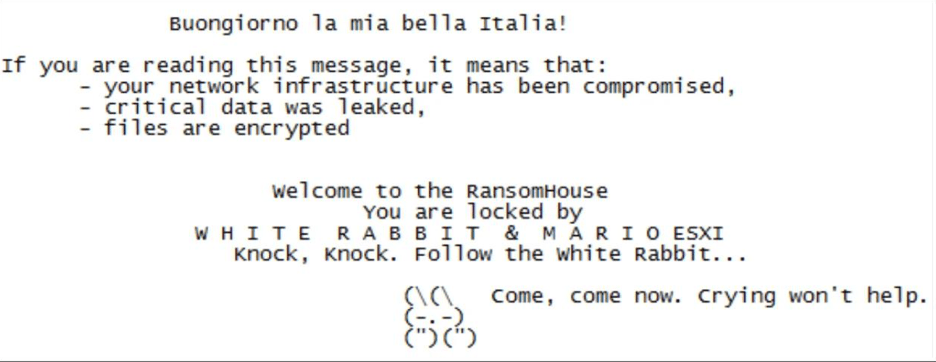
With its emergence approximately in late 2021, RansomHouse promoted itself as a Ransomware-as-a-Service (RaaS). Since the beginning of RansomHouse operations, it has been alternatively referred to as White Rabbit and Mario ESXi, creating confusion and adding layers of intrigue to their identity. The explanation, however, is simple: both Mario ESXi and White Rabbit strains are used by actors in their attacks. In ransom notes shared with the victims, the actors refer to themselves as Mario ESXi or White Rabbit and, in some cases, by all three names.
Source: Analyst1
Their first victim is believed to be the Saskatchewan Liquor and Gaming Authority (SLGA) which reported a ransomware attack on December 25, 2021. SLGA was also the first victim publicly claimed by RansomHouse, which was published on their data leak site on April 4, 2022. The SLGA, a Treasury Board, is responsible for overseeing the distribution, control, and regulation of alcoholic beverages, cannabis, and most gambling in the Canadian province of Saskatchewan. According to the SLGA investigation report released on November 10, 2022, the attackers exploited a critical vulnerability in the CMS platform software.
Forensic analysis revealed that the actors initially breached SLGA’s IT environment in November 2021. However, SLGA only became aware of the attack on December 25, 2021, when they received a ransom demand. As a result of this attack, “approximately 40,000 individuals were affected by this privacy breach, including current and past employees, dependents of the employees, and regulatory clients.”
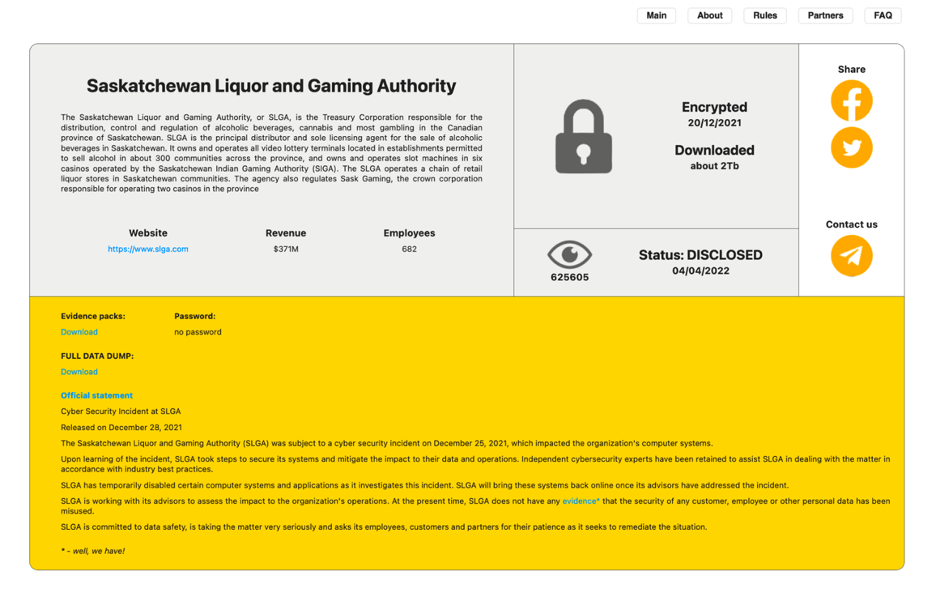
Source: RansomHouse DLS
The gap between December 25, 2021, when the actors initially contacted SLGA, and April 4, 2022, when they posted the company on their leak site, was a period during which they engaged in extortion. To bolster their double-extortion efforts, the actors utilized various methods, including a data leak site and reaching out to the media when negotiations stalled.
At some point during these three months of negotiations, the actors contacted CBC to disclose the breach and seek media visibility. “We tried to reach the company to provide them this information and to start negotiations. They said they don’t care about the problem,” claimed the individual, identifying themselves as Jason Walmart to a reporter. They shared a data sample purportedly stolen from SLGA, including bank records, budgets, contracts, employee data, and supplier agreements Negotiations seemingly made no progress. Eventually, RansomHouse published claimed stolen data on its leak site.
The narrative of victim blaming is clearly observed throughout RansomHouse’s operations. We will delve deeper into analyzing these tactics used by the group later. Let’s proceed to the next section, examining RansomHouse’s association with other groups. The wide and calculated actions taken by the actors during its very first case – SLGA and other following attacks clearly indicated that they had established a team that was well-experienced and had been operating for a significant period. The question arises: to which groups exactly RansomHouse associated, and to what extent?
RansomHouse & Other Groups: RagnarLocker, Dark Angels, Dunghill and More
Researchers have drawn connections between RansomHouse and other prominent groups, with one of them being Dark Angels first seen approximately in May 2022. On March 7, 2023, Will Thomas, a threat intelligence researcher at Equinix, observed similarities between the ransom notes of both RansomHouse’s Mario ESXi and Dark Angels. According to the analysis, similarities in wording were identified, accounting for approximately 84.3%.
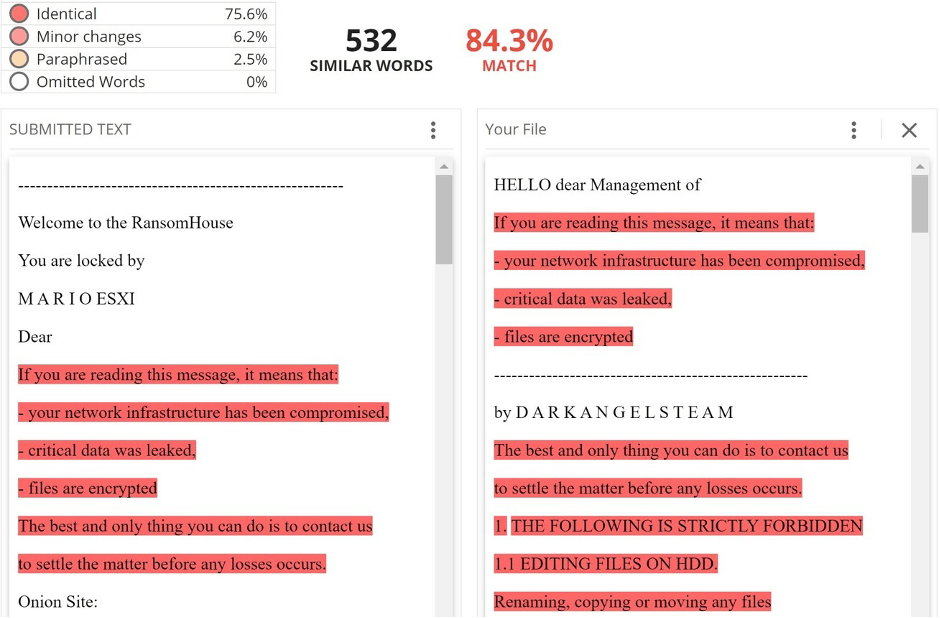
Figure 5: Similarities between ransom notes of RansomHouse and Dark Angels indicate matching in wording
Source: Will Thomas’ Twitter
Notably, both RansomHouse and Dark Angels were named one of the most active ransomware groups in 2023 by Chainalysis, a blockchain analytics company. Another valuable finding is the median ransom size versus its frequency of payouts, which shows that Dark Angels’ median payment size is close to USD 1.5 million, while the frequency of payouts stays relatively low. This means that Dark Angels generates higher profit with fewer payouts compared to other strains, such as Phobos for example. Phobos has the highest frequency of payouts, while its median size payment, which is less than USD 1,000, remains the lowest.
Based on the investigation of a known BTC address <bc1q0wf73xmcqkvrvs7tj49hznxqqgt6tp359gk0az>, by Analyst1, Dark Angels actors received nearly 38 BTC ransom payment (equivalent to USD ~1.5 million at the time of the transaction) on May 4, 2022. In comparison to a RansomHouse, a known BTC address <1MmkNa1gRUmVSocZic8wJhehef8NW4GzDZ> reported by Trellix and attributed to RansomHouse was used to receive a ransom payment in a similar amount of nearly USD 1.2 million received on December 12, 2023. According to the report, the initial ransom was set to USD 2.56 million with an apparent 50% discount agreed at the end.
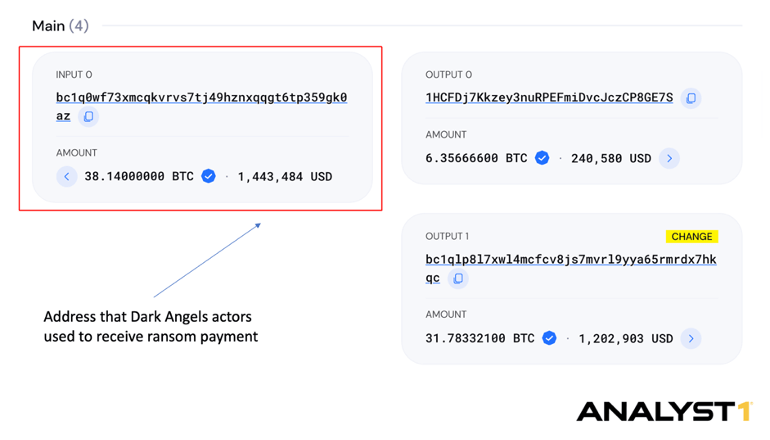
Source: blockchair.com
Johnson Controls International (JCI) which became one of the victims of Dark Angels shed light on connection between Dark Angels and two other groups: Dunghill Leak and RagnarLoker. JCI is a company specializing in manufacturing industrial control systems, physical security systems, and facility-related technology and infrastructure and does extensive business with U.S. federal agencies and the defense industrial base sector.
According to Bleeping Computer sources, actors stole over 27TB of confidential data and demanded USD 51 million to provide a file decryptor and to delete stolen data. As it was later disclosed by JCI through an SEC filing submitted in December 2023, an attack occurred during the weekend of September 23, 2023.
Based on the reporting, “The cybersecurity incident consisted of unauthorized access, data exfiltration and deployment of ransomware by a third party to a portion of the Company’s internal IT infrastructure.” The attack resulted in a significant financial loss of nearly USD 27 million, consisting of “expenses associated with the response to, and remediation of, the incident, and are net of insurance recoveries.” It is unknown if any of the portion of these USD 27 million in expenses was partially a ransom paid to actors.
The connection between Dark Angels and Dunghill Leak was established through investigation of a ransom note shared by Dark Angels with JCI. According to the ransom note shared by threat researcher Gameel Ali on September 27, 2023, with the remainder shared with Analyst1 later, it was identified that during its double-extortion phase, actors directed the victim to the Dunghill Leak data leak site.
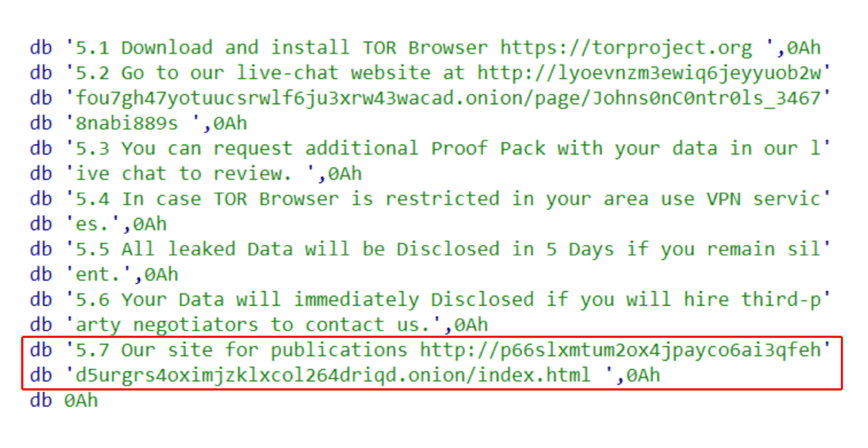
Source: Analyst1
The first victim was posted on the Dunghill Leak site in April 2024. Interestingly enough, the Dark Angels launched a separate data leak site at approximately the same time as the group’s appearance in May 2022; however, no victims were ever posted for several months of its existence. Instead, actors seemed to use a Dunghill Leak instead of where their victims are being directed, including the JCI attack.

Source: Dunghill DLS
In addition to the DLS, the Telegram channel “Leaks Directory” was registered on January 15, 2023, where actors would post claimed victims’ names and files with the stolen data. According to the Analyst1 cross-reference analysis of Telegram and Dunghill Leak DLS, posts and identified claimed victims match on both platforms. In some cases, entities were posted on the same day, while in others, they were first posted on Telegram and then on the data leak site, or vice versa.
For example, their first victim posted on DLS on April 24, 2024, was posted on their Telegram channel on January 23, 2024, nearly two months earlier. Their Telegram channel was also used to clarify some “confusion among researchers” about Dark Angels being associated with Babuk. On April 21, 2023, Dark Angels posted a message denying any associations with Babuk by stating that leaked Babuk code was adapted by them and that they have their “own product” for Linux and ESXi.
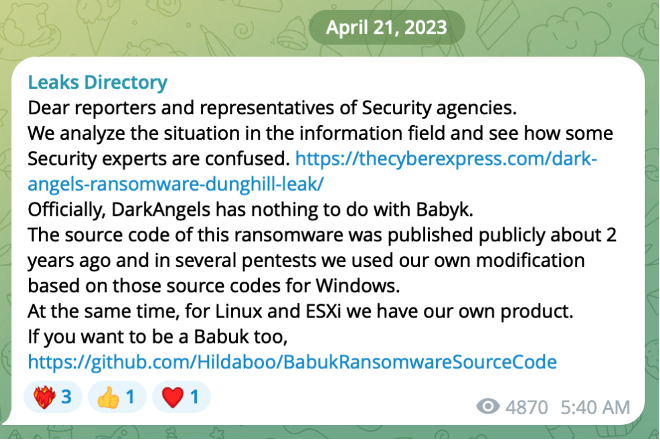
Source: Telegram
Another connection between RansomHouse (Dark Angels) and RagnarLocker was also uncovered during the investigation of the JCI attack. Similarities between Dark Angels and RagnarLocker were identified, with Dark Angels observed using RagnarLocker’s original ESXi encryptor in the JCI attack. Later, we will further discuss the potential association of actors from both groups as RagnarLocker was identified in one of the crossclaim cases with RansomHouse.
Indicators of associations between RansomHouse (White Rabbit & Mario ESXi), Dark Angels (Dunghill), and RagnarLocker groups suggest cross-collaboration among actors, with the high possibility of involving the same actors in operations of all three groups. The existence of such links might explain our findings of crossclaims between RansomHouse, considering their potential collaboration. In the following two sections, we will analyze crossclaim cases, also exploring the motivation behind data sharing among ransomware groups and its impact on incident response strategies.
Investigating RansomHouse’s Crossclaims
Crossclaims occur when the same victim is claimed multiple times by different ransomware groups on their DLS. Understanding the nature of crossclaims is crucial as it plays a pivotal role in guiding incident response actions effectively. Although we take threat actors’ claims with a high degree of skepticism considering established cases of false claims, this source overall provides a good understanding of actors’ victims’ preferences and overall activity.
Investigating the RansomHouse group, we analyzed a dataset of entities posted by the group from May 9, 2022, to February 28, 2024. Based on our findings, 11 out of 73 total victims were identified as being cross-claimed by other groups. We observed crossclaims cases between RansomHouse and Alphv/BlackCat, LockBit 3.0, BianLian, Snatch, Stormous, RagnarLocker, Abyss and CLOP.
Looking at the timeline of crossclaims, we observe two scenarios involving RansomHouse. In the first scenario, RansomHouse claims an entity initially, followed by other syndicates making subsequent claims. Entities involved in this scenario include BianLian, Snatch, Stormous, and Abyss. In the second scenario, RansomHouse claims the same entity after it has already been claimed by other groups, as seen in cases involving Alphv/BlackCat, LockBit 3.0, and RagnarLocker.
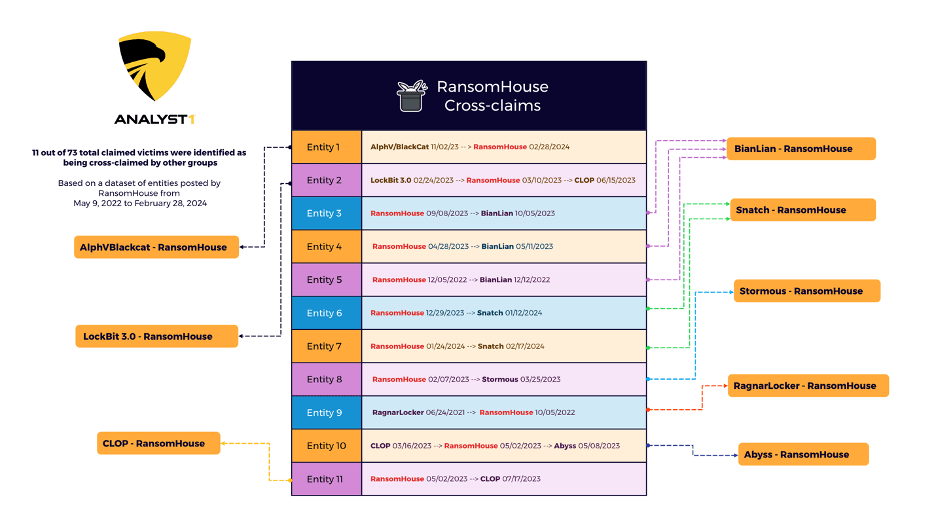
Source: Analyst1
Additionally, CLOP ransomware appears in both scenarios. However, we exclude the CLOP variable from our analysis (although such collaboration is still possible) of potential data sharing between groups, as all entities cross-claimed with RansomHouse were confirmed to be breached by CLOP in separate cases during the exploitation of a zero-day exploit of Progress Software’s MOVEit in May 2023.
LockBit, Alphv/BlackCat and RagnarLocker were identified as crossclaiming the same victims as RansomHouse among other groups. These cases follow the same scenario: LockBit 3.0, RagnarLocker, and Alphv/BlackCat claim the victim first and follow with a subsequent claim by RansomHouse.
For example, the collaboration between LockBit and BlackCat is not new, and we’ve seen such cases in the past. This cooperation extends to the sharing of infrastructure, including data leak sites. A noteworthy illustration of collaboration is the case of BlackMatter, formerly known as DarkSide, which transferred their victims to LockBit while undergoing a shutdown and rebranding process back in November 2021, eventually rebranding as Alphv/BlackCat later that year.
Source: BleepingComputer
Notably, a RansomHouse – Alphv/BlackCat crossclaim occurred during the time of another shutdown that BlackCat actors decided to make as the result of law enforcement actions. HAL Allergy was claimed by Alphv/BlackCat on November 2, 2023. Nearly a month later, on December 19, 2023, BlackCat’s Data Leak Site was prominently taken down, displaying a seizure notice. This occurred due to a joint international operation of law enforcement agencies. According to The United States Department of Justice (DOJ), as a result of the operation, the FBI offered a decryption tool to over 500 victims worldwide, with additional victims encouraged to come forward.
Almost two months after BlackCat’s claim, on February 28, 2024, RansomHouse claimed HAL Allergy. The company reported an attack confirming that on the morning of February 19, 2024, it was targeted by ransomware. It is unclear what strain was used to encrypt the victim’s network and whether BlackCat assisted RansomHouse in any way to access HAL Allergy. However, considering the established cooperation of BlackCat actors with other groups, the timing of both claims suggests that such an instance might have taken place.
The crossclaim involving RansomHouse and LockBit 3.0 presents yet another instance of potential collaboration. Delaware Life Insurance was claimed by LockBit 3.0 on February 24, 2023, and by RansomHouse on March 10, 2023, while also being claimed by CLOP on June 15, 2023. According to notifications shared with its clients, the company reported only two ransomware incidents in 2023: first between May 29 and May 30, 2023, attributed to the CLOP attack exploiting the MOVEit vulnerability, and second on February 9, 2023. As mentioned earlier, we are excluding CLOP crossclaims from our analysis due to the nature of the breach, which likely has no association with breaches of the same victim claimed by LockBit and RansomHouse.
Considering the timeline of the reported attack on February 9, 2023, and the subsequent claim by LockBit 3.0, it is likely that LockBit actors were responsible for the initial attack. The outcome of negotiations with Delaware Life Insurance is unclear, but the appearance of the company on the data leak site suggests that the victim refused to cooperate with the actors. Subsequently, the data may have been shared with RansomHouse, which then claimed the company on their data leak site approximately two weeks after LockBit 3.0’s initial claim.
It is possible that a single actor might utilize data under a different syndicate’s brands, a common occurrence in the realm of RaaS, where affiliates often partner with multiple groups. However, we are more inclined to believe in a well-established relationship between groups connected on multiple levels rather than just one single actor working with both syndicates.
It is also important to consider that these groups are geopolitically aligned with Russia, suggesting that their composition belongs to the same community. One of the key characteristics of the Russian ransomware ecosystem is a collectivist mindset and close interpersonal relationships that serve as the foundation for their “business” operations. Given the current geopolitical climate, actors may find themselves increasingly connected and supportive of each other, pooling their resources against entities they perceive as the state’s enemies.
The crossclaim between RagnarLocker and RansomHouse presents an intriguing case that suggests potential data sharing between two groups or even the involvement of the same actors in the operations of both groups. Like LockBit 3.0 and Alphv/BlackCat, RagnarLocker initially claimed a victim, with RansomHouse later doing the same. Specifically, Entity #9 on our graph, a Taiwanese chip maker ADATA was first claimed by RagnarLocker on June 24, 2021, on its data leak site following a ransomware attack on May 23, 2021, during which the entity refused to pay a ransom, resulting in a data leak.
Subsequently, on October 5, 2022, RansomHouse made a claim on ADATA, alleging possession of 1TB worth of sensitive data. Three days prior to that, actors also claimed ADATA as a victim on their Telegram channel. However, in a statement to a BleepingComputer, ADATA denied the claim of a RansomHouse attack, asserting that the leaked files were from a May 2021 RagnarLocker breach, during which 1.5TB of data was stolen.
The exact nature of the data presented to ADATA by RansomHouse remains unclear, raising questions about whether it was the same data leaked/stolen previously by RagnarLocker. In addition to the scenario where RansomHouse actors are not in fact linked to RagnarLocker and acquired the data leaked from the ADATA breach in 2021, falsely presenting it as a new attack, we also explore an alternative scenario to address such coincidence of this crossclaim.
One possibility is that there was collaboration between actors, involving the sharing of data either freely or for a fee between two ransomware groups. Alternatively, it’s possible that the same actor(s) who previously operated under the RagnarLocker brand eventually transitioned to RansomHouse.
The transition could have occurred during the arrests of RagnarLocker actors in October 2021 across multiple countries, including Ukraine and France. Despite RagnarLocker continuing its operations until October 2023, when its data leak site was seized by law enforcement, some RagnarLocker actors might have moved to other groups during the initial arrests in 2021. There is also a possibility that RansomHouse emerged as a new project for actors involved in RagnarLocker operations as they sought to continue their criminal activities under a different brand.
It can also explain instances of similarities between Dark Angels, which is suspected to be closely associated with RansomHouse, and RagnarLocker. Dark Angels was observed using RagnarLocker’s original ESXi encryptor in the JCI attack mentioned earlier in the report. While similarities in source code do not definitely confirm the involvement of the same actors in the operations of both groups, as it could have been purchased from actors, the coincidence of both groups claiming the same victim might potentially suggest such a scenario.
Moving forward to BianLian, we observed three instances of crossclaims to be made by these two groups, with RansomHouse first claiming the victim and then BianLian claiming the same entity. BianLian has been operating since approximately June 2022. The indication of potential association and involvement of the same actors in both RansomHouse and BianLian operations was reported by Resecurity on December 15, 2023, which noticed the same email used by both groups in their communication with victims. Thus, swikipedia@onionmail[.]org was observed to be shared by RansomHouse with one of the victims, while the same email was attributed by CISA to BianLian. Artifacts such as emails and other indicators are valuable evidence for establishing connections between multiple groups within the ransomware landscape, which is likely the case in BianLian-RansomHouse’s potential association.
In the case of Abyss-RansomHouse, there was a single claim concerning AvidXchange, a financial software company based in the US. The company has claimed a total of three times in 2023: one by CLOP on March 16, 2023, another by RansomHouse on May 2, 2024, and one by Abyss on May 8, 2023. According to the Office of the Maine Attorney General, the breach occurred on March 2, 2023, and likely referred to a CLOP attack based on the data leak timeline. No other official reports on additional attacks occurring in 2023 were found.
The connection between RansomHouse and Abyss remains unclear, as does whether the claimed attacks on AvidXchange were separate incidents or if, in fact, they ever took place. Abyss shares many similarities with RansomHouse, including using different strains for both Linux and Windows systems. Given the timeline of claims and similar modus operandi of both groups, there is a possibility of collaboration between syndicates.
While it is possible that a victim may be targeted independently by separate actors exploiting different vulnerabilities, the prevalence of cross-claims suggests a deeper underlying dynamic: collaboration and data sharing among threat actors. Our investigation into a potential link between RansomHouse and the above-mentioned groups is ongoing. In the next section we will look at the intriguing case of potential collaboration between RansomHouse with Stormous and Snatch and involving influence operations, which we uncovered during our investigation.
RansomHouse, Stormous & Snatch: Ransomware, Hacktivist-Like Hybrid
We’ve singled out Stormous and Snatch for a specific reason: their involvement in influence operations introduces a different dimension. Our previous research on Snatch shed light on its activity. From our observations, Snatch actors appear to engage in hacktivist-like operations, leveraging their ransomware resources to conduct covert influence campaigns, primarily targeting Europe and the United States. Snatch actors have openly admitted to engaging in data reuse, claiming to “specialize exclusively in leaked sensitive data” and collaborating with other ransomware groups responsible for data breaches.
Interestingly enough, Snatch openly admitted its partnership with RansomHouse while commenting on an incident involving Banco Promerica de la República Dominicana, a victim claimed first by RansomHouse on December 29, 2023, and then by Snatch on January 11, 2024. On January 12, 2024, Snatch actors responded to an article published by The Cyber Express, highlighting a dual attack by RansomHouse and Snatch, stating, “That is not a contradiction between two groups – but two partner groups working together.” Not only did Snatch post details of the victim on its data leak site, but it also shared information about the entity on its Telegram channel. Over five messages posted from January 12, 2024, to June 2, 2024, Snatch shared sensitive information related to their victim, including personal details of individuals associated with it.

Source: Telegram
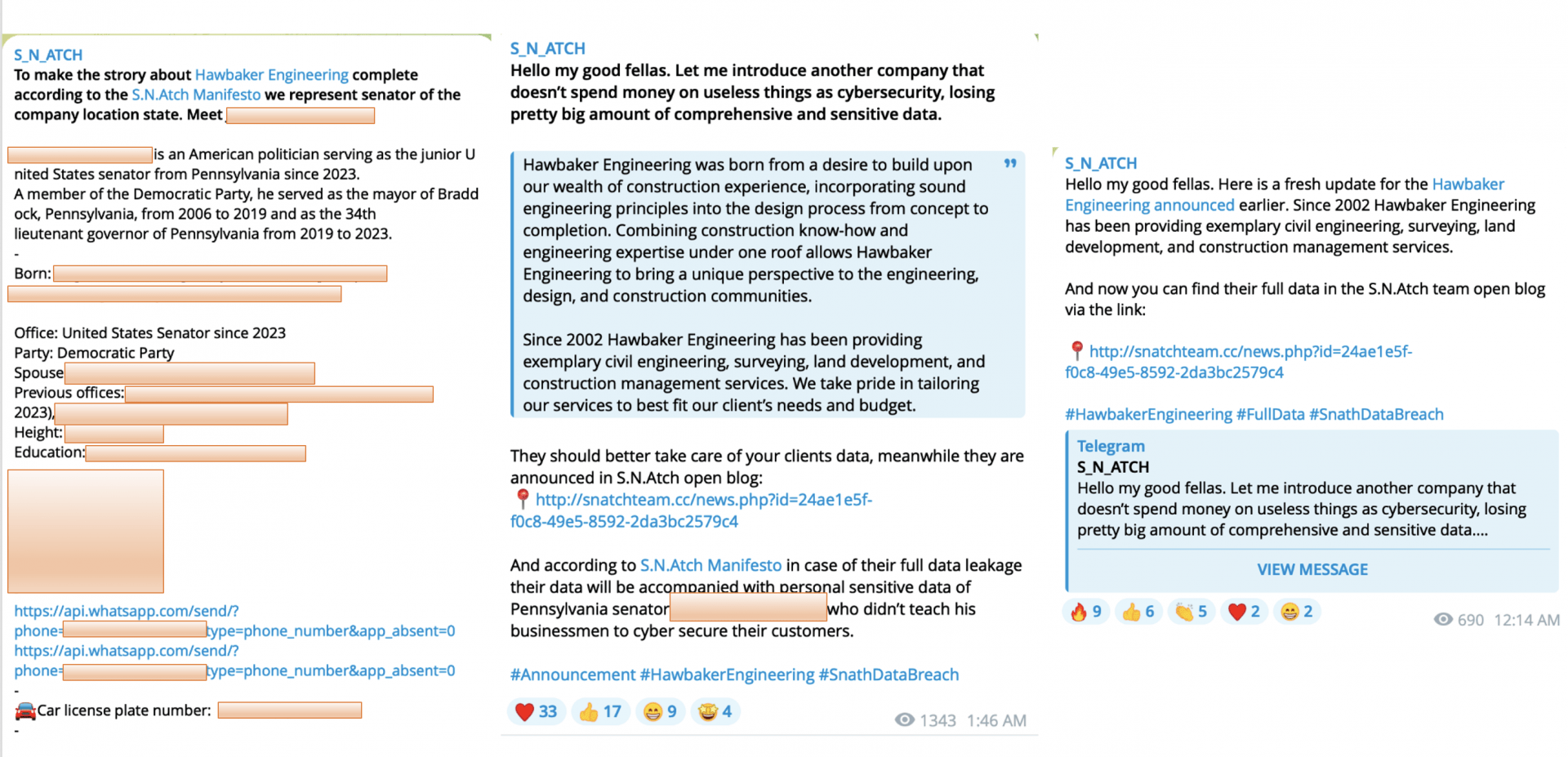
On February 17, 2024, Snatch posted Hawbaker Engineering on its data leak site and Telegram channel, marking another crossclaim with RansomHouse, which posted the entity earlier on January 24, 2024.
During this period, from February 14, 2024, to February 26, 2024, Snatch shared sensitive information related to the company in a series of messages. This wasn’t merely a routine ransomware leak; in typical Snatch fashion, it targeted government officials associated with the state where the company is located. The message conveyed in these posts once again criticized the entity and associated individuals, aligning with the so-called Snatch manifesto that justifies their actions under the guise of addressing “weak security practices.”
From Snatch Manifesto: “Business and power are united and go hand in hand. And each leak has its own name and face, both from the side of the business that allowed it and from the side of the authorities covering this business. That’s why from now on each of our publications will be accompanied by personal data of presidents (owners of companies) and personal data of representatives of authorities assigned to this region.”
Source: Snatch Telegram channel
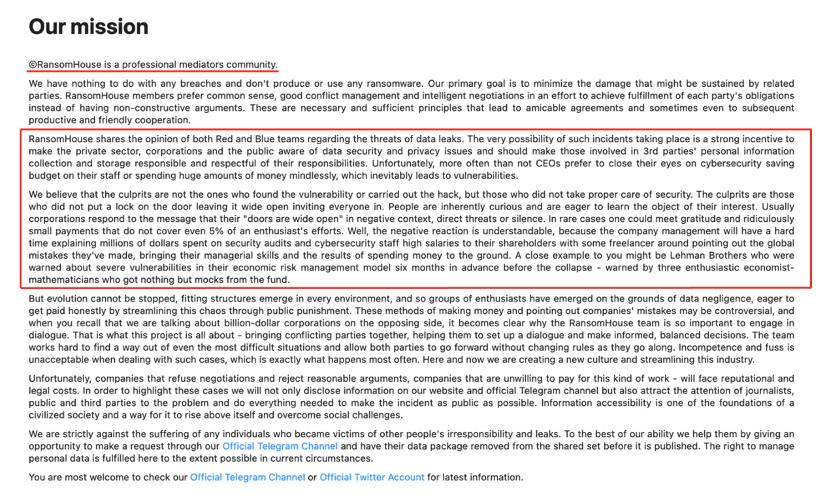
Two groups also seem aligned with the narratives of victim-blaming they are pushing to the public. RansomHouse, similar to Snatch, claims that its primary goal is to ensure digital safety by educating its audience on various subjects. On their leak site’s mission section, RansomHouse actors describe themselves as a “professional mediators community” committed to safeguarding personal information. They assert, “We believe that the culprits are not the ones who found vulnerabilities or carried out the attacks, but those who did not prioritize security.”
Source: RansomHouse DLS
To increase visibility, RansomHouse takes this victim-blaming narrative a step further by pushing a similar message through their X account, tagging the platform’s CEO, Elon Musk. In a post dated April 19, 2023, the actors state, “We want to use your social media service to let people know how poorly their data is being treated while many companies do not wish to tell the truth.”
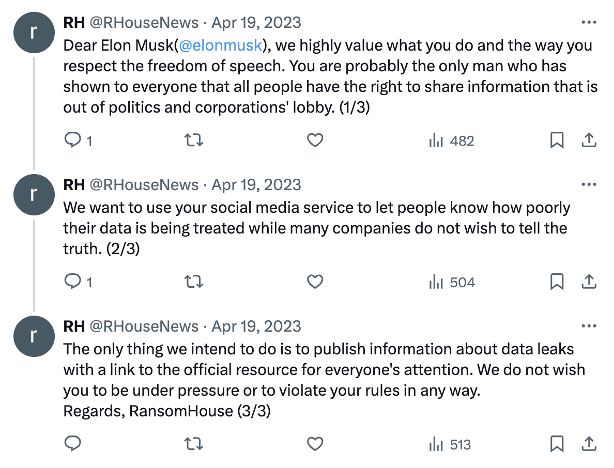
Source: Twitter
The same narrative is also evident in the announcement of RansomHouse’s partnership on its data leak site’s “Partners” page. Here, Database Cartel and Ares Leaks are called their “partners related to information disclosure” activities. This tactic clearly serves as an attempt to justify their criminal actions of disclosing personal data as a form of punishment for victims who failed victims of their attacks.
Upon investigating Ares Leaks and Database Cartel activities, we discovered that their primary operation revolves around a stolen data market. These groups frequently post updates about their claimed victims and offer the stolen data for sale on their Telegram channels. Initially, Ares Leaks also operated a forum, which now appears inaccessible.

offering stolen data on Telegram visible in the bottom image
Source: RansomHouse DLS/Telegram
We also observe a very similar operational, hacktivist-like activity and tactics employed when analyzing Stormous. In addition to the website on Tor serving as a data leak site, the group also established a presence across Telegram and X (Twitter), with their accounts eventually being disabled on both platforms. It is worth adding that their DLS also became inaccessible approximately on May 11, 2024, and still is as of the day of this report on June 6, 2024.
Such an alignment in tactics might also indicate potential cooperation and explain what initially drew our attention: a case of cross-claims observed between Stormous and RansomHouse. According to our analysis, there is one instance of a cross-claim involving The Dubai Gold & Commodities Exchange (DGCX), a UAE entity claimed first by RansomHouse on February 7, 2023, and then by Stormous on March 25, 2023. A cyber incident was confirmed by a DGCX spokesperson on February 9, 2023, stating that an unauthorized third party accessed some files, but it did not impact day-to-day operations or its trading platform.
When exploring potential connections between groups, we found a noteworthy detail that may indicate such a scenario. Specifically, a ransom note was submitted on VirusTotal on April 28, 2024, by Dark Angels (whose association with RansomHouse we’ve established earlier), allegedly extorting one of their victims, Ingersoll Rand.
However, the most intriguing aspect emerged when we checked Dunghill Leak, which Dark Angels included in their note, and found no claims of Ingersoll Rand. What we found instead was Stormous claiming this entity on March 27, 2023, on its data leak site. Although the possibility of Stormous and RansomHouse targeting the same company theoretically might exist, it is likely that two groups were cooperating with each other, including this particular case or, in additional cases, are likely subgroups of a bigger group.
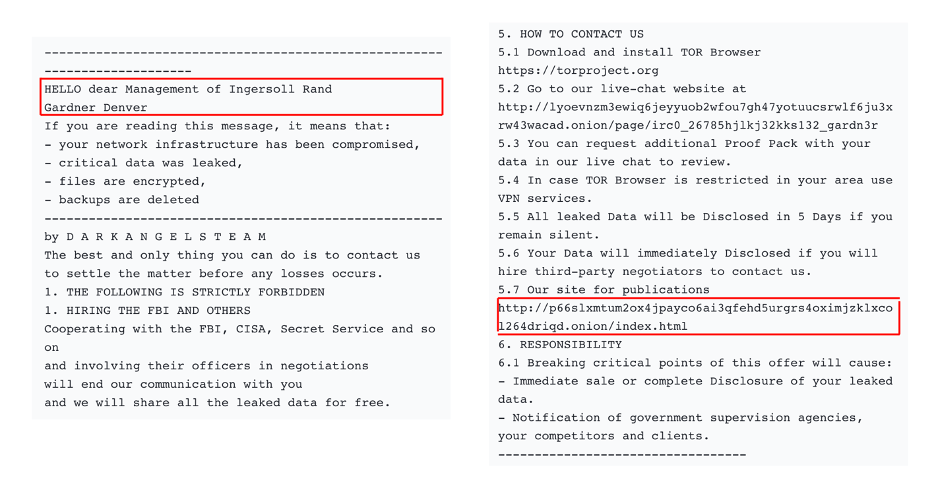
Source: Virus Total
Given the suspected affiliation between Dark Angels and RansomHouse and the possibility of them sharing data and resources, such an intersection makes sense. This alignment is further supported when examining the tactics used by these groups. In particular, Dark Angels/Dunghill and RansomHouse demonstrate many similarities in their position, employing a victim-blaming strategy.
Their data leak site’s “About Us” page states, “We are an international team of technical specialists conducting research in the field of information security. We are not interested in politics and therefore do not cooperate with governments and law enforcement agencies. Our main goal is to make the world more secure. Yes, security costs money, and so does our time. That’s why we offer our services on a fee basis.”
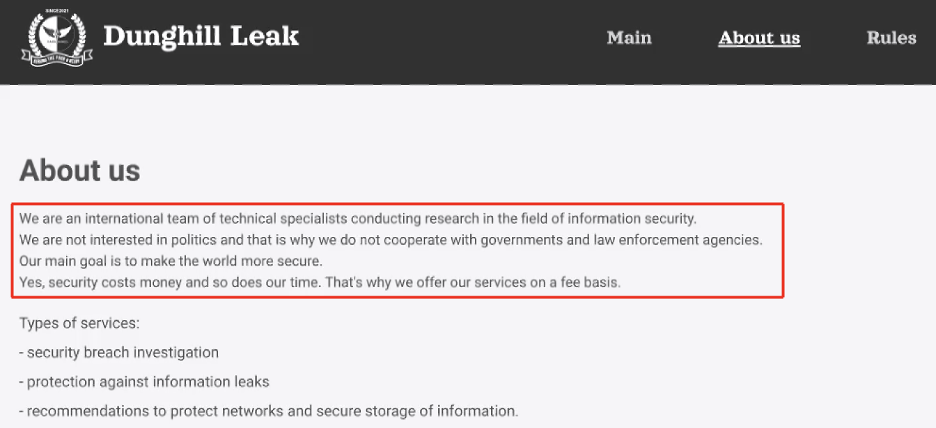
Source: Dark Angels DLS
When examining Stormous’s timeline and nature of operations, the group emerged around mid-2021 initially as a typical ransomware group engaging in RaaS (Ransomware-as-a-Service). Over time, however, they adjusted their operations and became increasingly vocal about their political stance.
On March 1, 2022, four days after the invasion of Ukraine started, Stormous posted a message: “The STORMOUS team has officially announced its support for the Russian government. And if any party in different parts of the world decides to organize a cyber-attack or cyber-attacks against Russia, we will be in the right direction and will make all our efforts to abandon the supplication of the West, especially the infrastructure. Perhaps the hacking operation that our team carried out for the government of Ukraine and a Ukranian airline was just a simple operation but what is coming will be bigger!!!”
In July 2023, Stormous publicly aligned themselves with GhostSec, a hacktivist-like group. Both later became part of the so-called “Five Families” in August 2023, which included four hacktivist groups: GhostSec, ThreatSec, SiegedSec, and BlackForums, a forum dedicated to the selling of stolen data. An overview of their activity suggests their alignment with various causes, including pro-Palestine, pro-Russia, and other geopolitically aligned actors, often correlating with global events and conflicts. In this research, however, we deliberately refrained from focusing on the activity of these groups, including the geographical distribution of entities claimed by actors. Instead, we prioritize the investigation of the infrastructure involved in the operations of these groups, which lays the groundwork and provides a logical explanation of the cooperation between ransomware and hacktivist-like entities.
The integration of ransomware into hacktivist-like operations was publicly introduced in July 2023 through the announcement of a joint project, StmX|GhostLocker, between GhostSec and Stormous, declaring a ransomware/hacktivist alignment and pooling of resources. “We’re very proud to announce with our continuous work together the new blog that belongs to us, stormous, and the remaining partners.”, a Ghost Telegram message said on August 20, 2023. On May 15, 2024, GhostSec announced that they would no longer participate in ransomware and shift back to pure hacktivism. “To be 100% clear all this means is our full focus and shift back into pure hacktivism/Political hacking.”, they added in the following message.
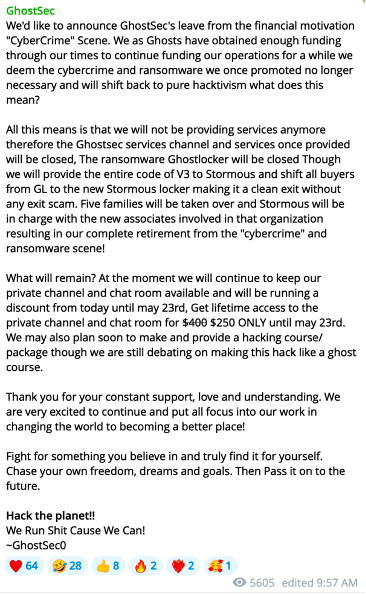
Source: Telegram
This announcement is unsurprising considering the observed behavior of such hacktivist-like groups. This underscores a complex ecosystem where actors frequently launch new projects, shut down others, and announce new partnerships under different names. These maneuvers serve dual purposes: evading detection by researchers and law enforcement and projecting a larger community presence than what actually exists. This strategy also serves the purpose of obscuring the clear collaboration between ransomware groups that supply stolen data to these hacktivist-like entities.
When examining the operations of RansomHouse with its suspected relationships with Dark Angels, as well as Snatch and Stormous, we observe a well-structured model where resources are efficiently combined between groups and utilized across ransomware, influence operations camouflaged as hacktivism and data markets. Considering the ransomware operations involved, the presence of data markets is not coincidental, as it signifies a deliberate integration of ransomware into broader activities.
BlackForums, announced as a part of Five Families, operated from approximately April 2023 to January 2024, after which it was replaced by a new forum called SecretForums. The founder and admin, known by the alias “Astounding,” posted a detailed graph explaining the project’s evolution during its existence. “I wanted to give out a bit more of an insight to BlackForums and SecretForums so i have created a timeline (it isn’t the whole timeline). I made this for the new comers and OGs to see how we operated.”, Astounding said on Telegram.
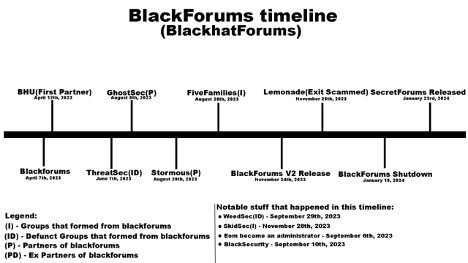
by its Admin Astounding
Source: Telegram
The SecretForums, launched in January 2024, is currently active with approximately 4,364 registered members and a total of 1,377 threads across various sections such as “Hacking,” “Leaks,” “Coding,” “Marketplace,” “Cracking,” and “Social” as of May 22, 2024. The involvement of data markets also highlights a particular framework in place, featuring data markets that not only secure additional ransomware revenue streams but also serve as a public justification for groups like Snatch and Stormous to claim ownership of data supposedly shared by other groups. While these groups present an illusion of open data access, the shared data is likely carefully curated to tailor information against specific entities of interest.
Source: Analyst1
Additionally, SecretForums maintains a presence on Telegram through its channel “SecretForums Propaganda.” An ironic detail is the forum’s attempt to solicit donations for their project despite the substantial revenue likely generated from selling stolen data. This gesture may not purely be driven by greed but rather an attempt to align with the perceived image of hacktivist-like groups that these modern Frankenstein ransomware/hacktivist hybrids seem to embody.

Source: Telegram
This hacktivist-like behavior is not coincidental but rather a carefully planned strategy. Another example is a ransomware attack claimed by Five Families on September 29, 2023. Stating Ortambo district in South Africa as a victim, the actors asserted they had access to the data of its citizens and government officials. They demanded a ransom of USD 10,000, publicly sharing a BTC address for ransom. We emphasize the deliberate public sharing of a BTC address. In typical attacks, ransom addresses are kept private and shared with the victims in a closed chat. Exposing the address publicly indicates an attempt to garner attention and visibility rather than purely financial motivation.
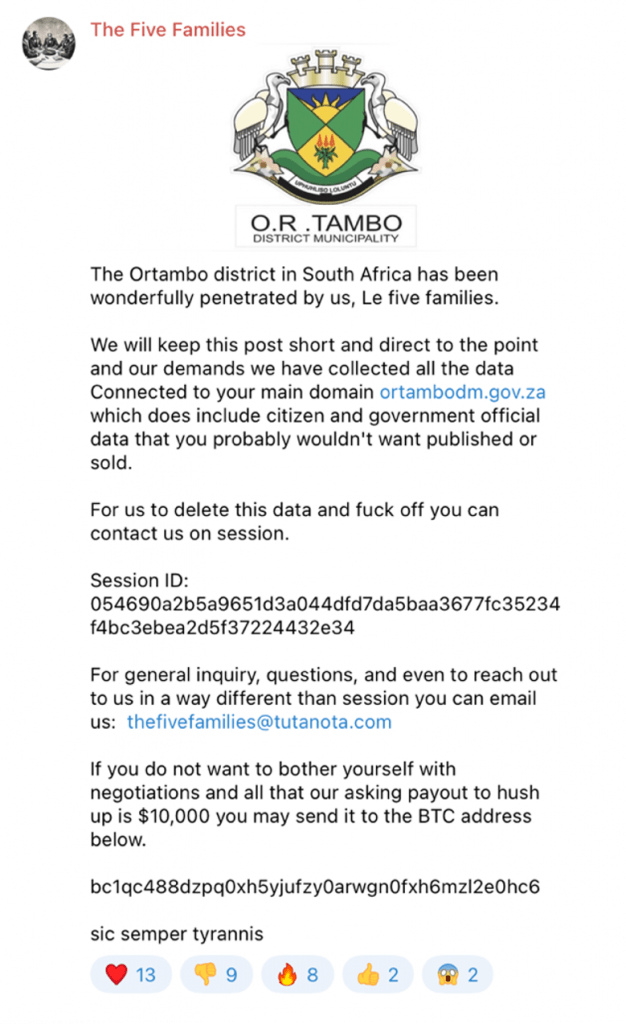
Source: Telegram
With this extensive activity, the question arises: what are these actors’ motivations, and to whom can these groups be attributed? Let’s analyze this in the next section.
Attributing Ransomware/Hacktivist Activity: What Are Motivations?
Based on the observed activities, it is evident that these groups are attempting to present themselves as hacktivist organizations by adopting typical characteristics associated with hacktivist activities: making political statements, soliciting donations, maintaining a strong social media presence, and creating an illusion of a larger group to attract public engagement and influence public opinion.
The reality behind these operations likely involves a well-established workflow: initial ransomware attacks likely involve Dark Angels and RansomHouse acquiring data, which is then passed down the chain. Snatch and Stormous, evolving into hybrid ransomware/hacktivist groups, repurpose this data for covert influence operations under the guise of hacktivism.
In the graph below, we categorized groups based on their observed activities, suggesting that many may be subgroups of a larger entity. Dark Angels and RansomHouse are primarily classified as ransomware operators, while Snatch and Stormous are dual-labeled as both ransomware and hacktivist groups. By categorizing them as hacktivists, we highlight their distinctive approach, where influence operations are disguised under hacktivist-like activities.
The graph also illustrates Stormous’s affiliation with recognized hacktivist groups as part of Five Families, which are involved in the joint StmX|GhostLocker ransomware project. Additionally, it identifies entities operating as Data Markets in two instances: BlackForums and SecretForums for Five Families and Ares Leaks and Database Cartel for RansomHouse.
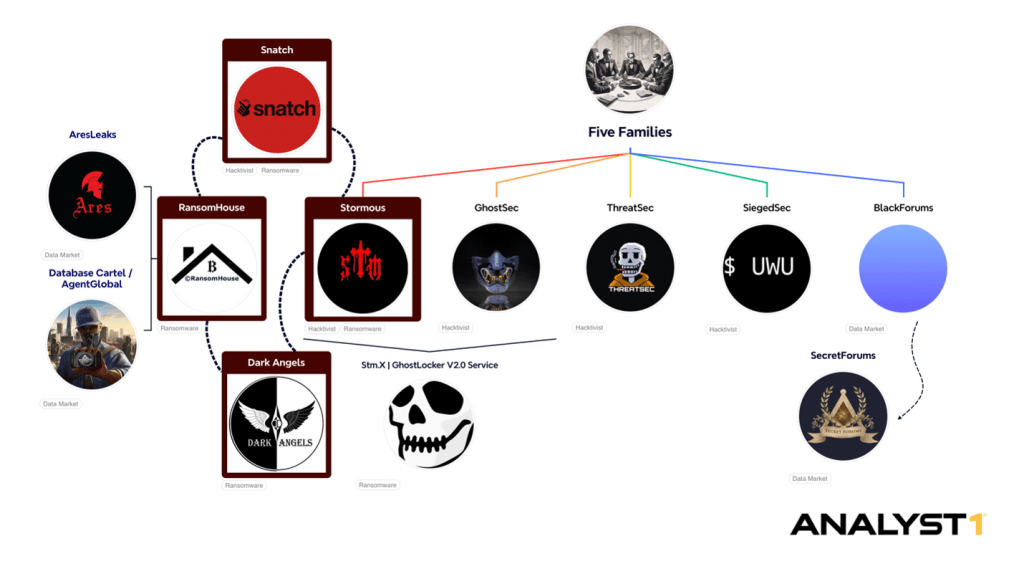
Source: Analyst1
Identifying a geopolitical alignment with a particular state is crucial to analyzing these groups’ activities and predicting their operations’ trajectory. Drawing upon our knowledge and investigation of these groups’ activities, it’s evident that many syndicates identified in cross-claims with RansomHouse, including Snatch and Stormous, are predominantly composed of Russian-speaking actors with a geopolitical alignment towards Russia.
Based on our previous research on Snatch, attribution analysis suggested they have roots in a Russian region for two primary reasons. Firstly, the group comprises Russian-speaking actors, as evidenced by the language used. Additionally, various artifacts point to this connection, such as using a command and control (C2) server hosted on a Russian bulletproof hosting service to execute attacks on their targets. Furthermore, according to a CISA report on the group, IP traffic analysis from event logs provided by victims indicates that Snatch establishes connections originating from servers based in Russia and through other virtual private network (VPN) services.
Similarly, in the case of Stormous, our investigation indicates a likely geopolitical alignment with Russia. Stormous, in particular, has always been vocal regarding its support of the Russian state. “We are designing our own ransomware (StormousX) which will be a corporate hell! Another point, we will launch our dark web site (.onion) this month. There is also a shop where we can sell the data of some important companies! Our own goals: America 80%, Ukraine 60%, India 58%, Peru 50%, Vietnam 12%).”, reads a message posted on the Stormous Telegram channel on July 2, 2022. Among their affiliates, rules later listed on their DLS would include a warning not to attack Russia and Russia’s neighboring countries, indicating a geopolitical alignment with the Russian state.
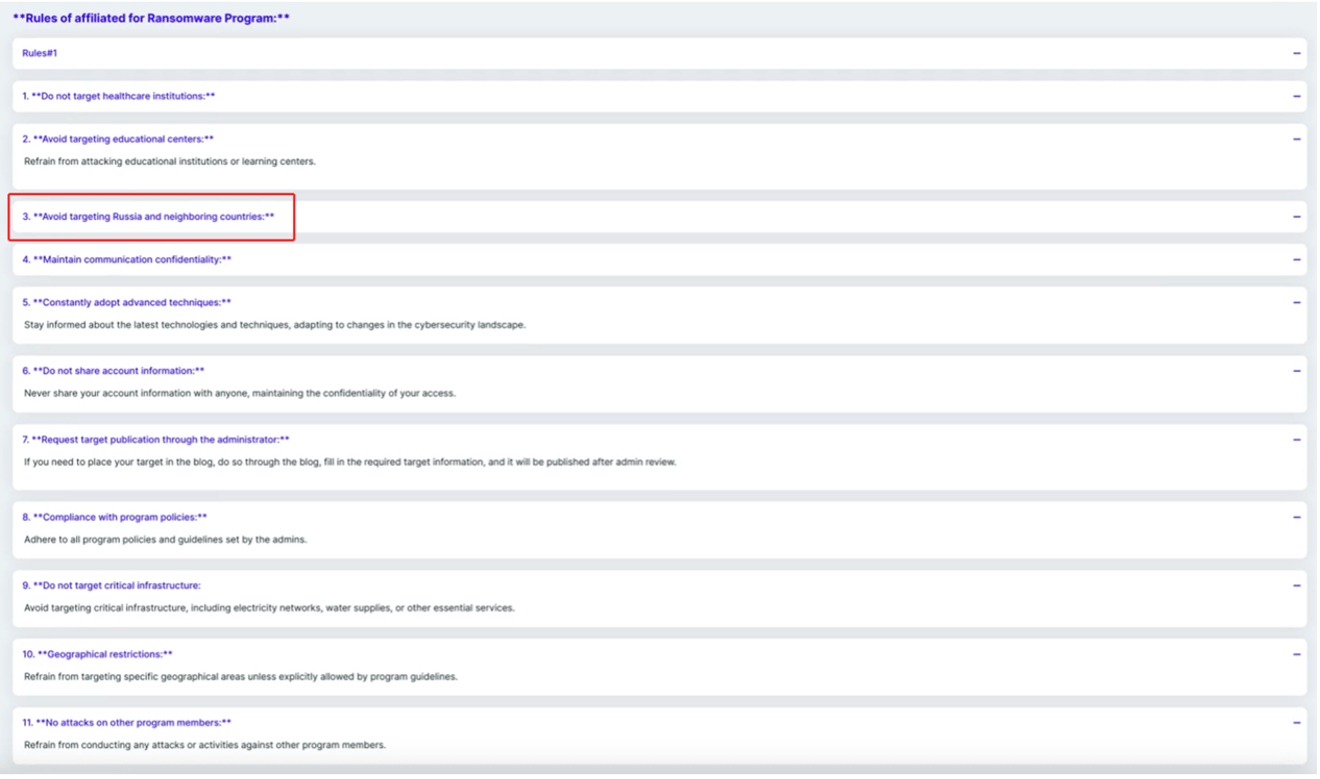
Source: Stormous DLS
The increased use of social media is another tactic adopted by hacktivist-like groups, particularly with the emergence of hybrid operations by groups like Snatch and Stormous, which exhibit hacktivist-like activities alongside traditional ransomware operations. Many of these groups now maintain a robust presence on platforms such as Twitter (now known as X) and Telegram, using these channels to disseminate their messages and narratives, including information about victims and narratives that often involve victim blaming.
Analyzing these groups’ activity across social media provides valuable insights into their alignment with particular states. Such geopolitical alignment can be explored by examining their portrayal by pro-Russian media and the narratives propagated therein. A closer examination involves tracking the frequency and amplification of content these hacktivist-like groups share within large pro-Russia news channels which are pivotal in amplifying narratives that align with Russia’s geopolitical agenda.
The overall support by pro-Russia media for geopolitical agendas, particularly in contexts such as the Russia-Ukraine conflict, offers extensive justification for the state’s actions. Telegram, in particular, has emerged as a significant communication channel, competing with traditional media and serving as a potent tool for disseminating narratives to the broader public. Pro-Russia channels disseminate messages portraying defenders against perceived enemies of the state, contributing to a wider narrative of resistance and defense aligned with Russia’s interests.
In recent years, particularly since the invasion of Ukraine, these defenders also include Russian hackers, a phenomenon that has gained prominence within Russia since 2016 with allegations of involvement in the US election. Their positive image has increased significantly since the invasion of Ukraine, with their activities perceived as supporting the broader agenda of the Russian state. Pro-Russia media channels often portray hacker groups favorably, highlighting their actions as part of a larger struggle or defense against adversaries.
Channels like Mash (with approximately 2.9 million subscribers) and Avia Pro (with around 55 thousand subscribers) have included coverage of AresLeaks, a group announced as a partner by RansomHouse. These channels shared documents and details of sensitive information allegedly stolen from US government entities and individuals in claimed attacks in a series of messages.
“Thanks to the hacking of American military base servers by Russian hackers from AresLeaks,” and “The data is from AresLeaks,” “Brothers, we learned all this wonderful information thanks to the great and terrible hacking of the servers of American military bases by our beloved Russian hackers from AresLeaks” are among the messages shared by Mash and Avia Pro. These portrayals celebrate the hackers’ actions, presenting them as uncovering valuable information and acting heroically to support Russia’s interests.
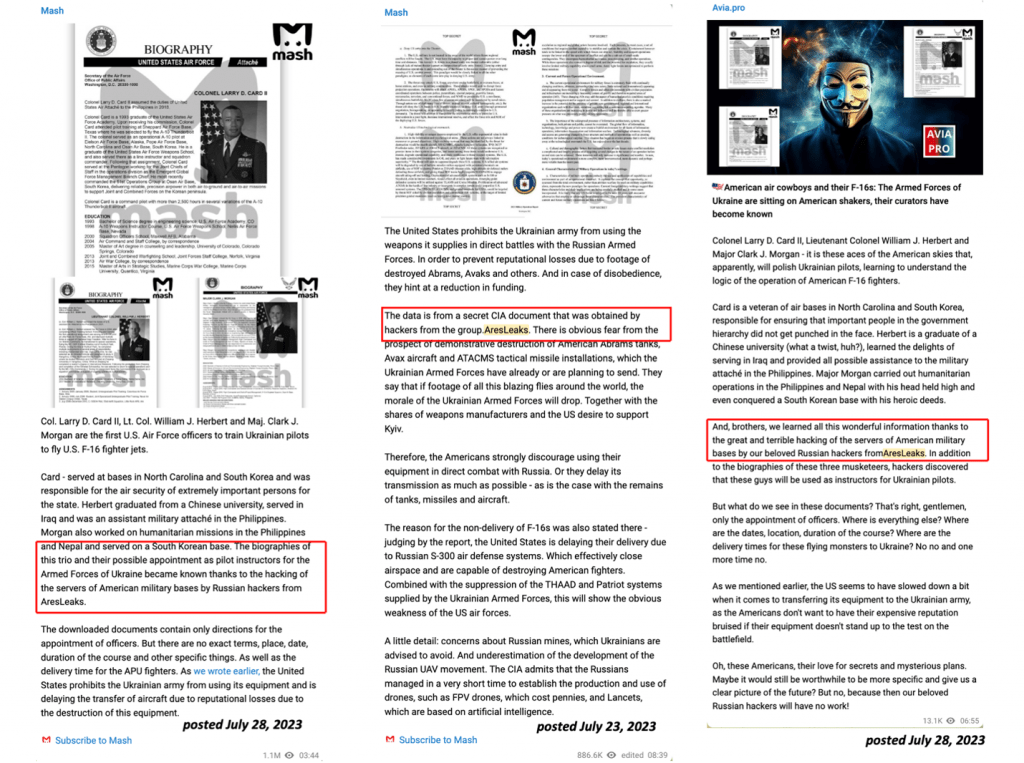
Source: Telegram
The question of state involvement remains uncertain and requires additional strong evidence to make a definitive judgment. However, considering the overall observed activity, including the visible presence of substantial resources and high levels of coordination that align with the Russian state’s broader geopolitical agenda, it is likely possible.
The alignment of their activities with state objectives, the support from pro-Russian media channels, and the historical precedent of state-supported cyber activities all point towards the likelihood of potential state involvement. As such, understanding the potential state backing behind these groups is crucial for developing effective countermeasures and mitigating the impact of their operations.
Conclusion
The analysis of data sharing among ransomware groups highlights the emergence of new challenges in cybersecurity. Traditionally, ransomware attacks involve encryption and data exfiltration, with some cases involving data theft without encryption. However, the collaboration among groups like RansomHouse, Dark Angels and others introduces a novel approach where stolen data is recycled among threat actors, leading to deceptive extortion attempts that simulate new attacks. This phenomenon underscores the importance for organizations to enhance their cybersecurity measures to protect against initial breaches and mitigate the risks posed by subsequent misuse of stolen data.
Moreover, the involvement of groups like Snatch and Stormous in influence operations, camouflaged under the guise of hacktivism, adds another layer of complexity. These operations target sensitive data and aim to manipulate public opinion and influence geopolitical narratives. Defending against these threats requires a comprehensive approach that includes robust cybersecurity defenses, rigorous data protection protocols, and strategic responses to mitigate reputational damage at both governmental and individual levels.
Addressing these challenges will necessitate collaboration between cybersecurity experts, law enforcement agencies, and policymakers to develop effective strategies that can adapt to the evolving tactics of ransomware and hacktivist-like groups. Organizations can better safeguard their data, integrity, and resilience in an increasingly digital and interconnected world by understanding and countering these sophisticated threats.