This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Analyst1 Spotlights
Improve Your Security Operations
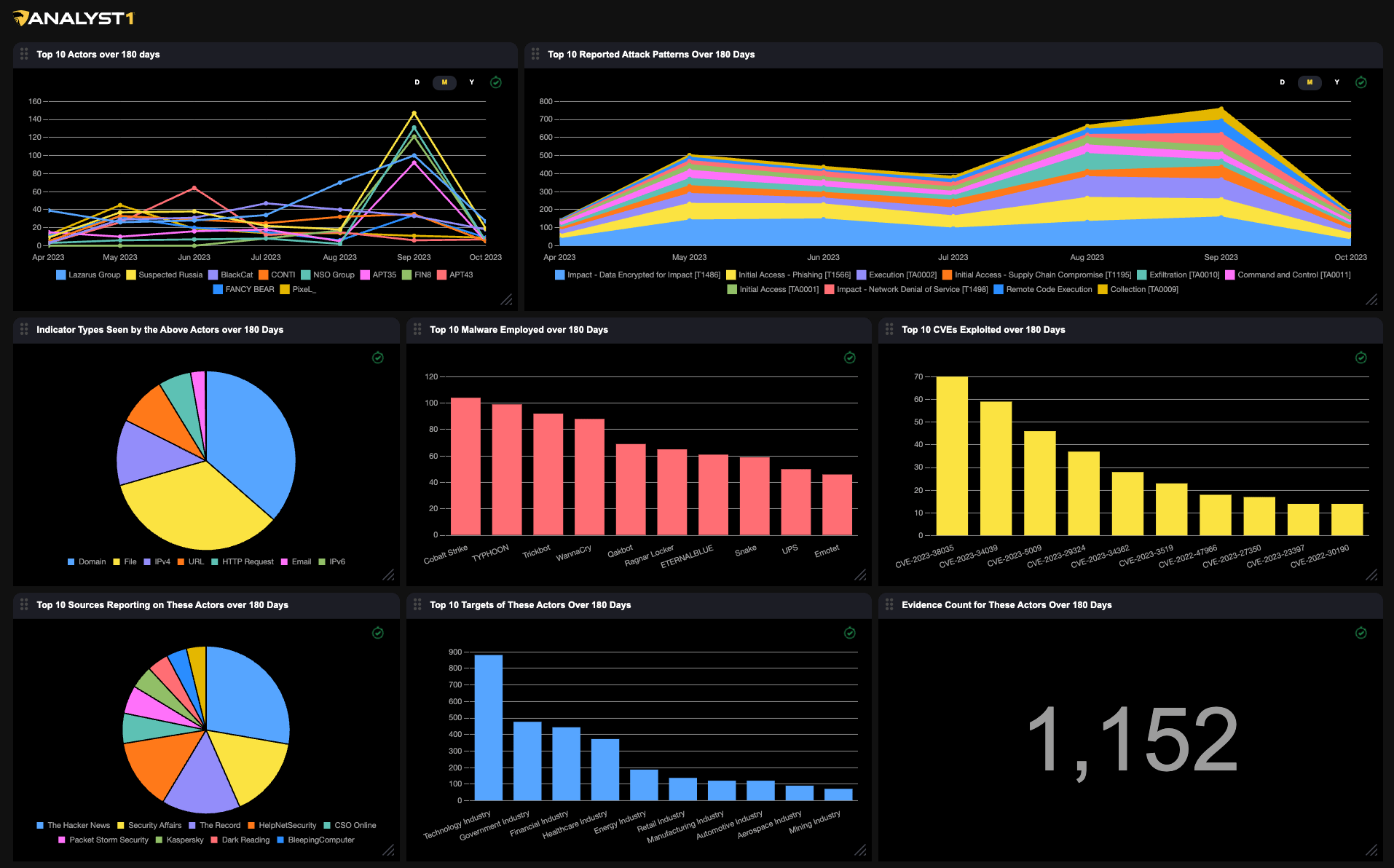
THREAT ACTOR REPORTING
Recognize recurring patterns in observed threat activity
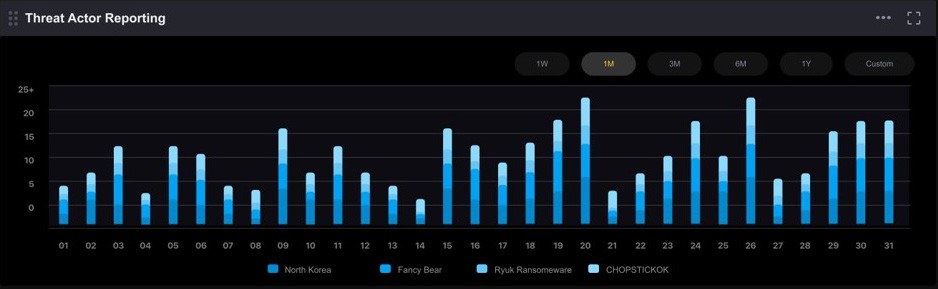
VULNERABILITY EXPOSURE
Track the assets you own that are vulnerable to the exploits of threat actors
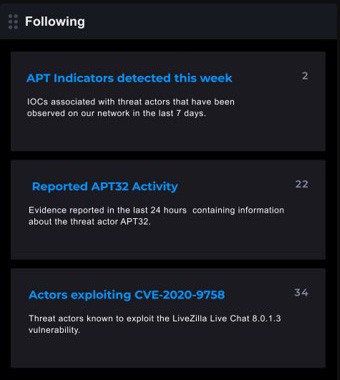
FOLLOWING
Receive alerts on important information that interests you
Track Targeted Industry’s
Stay informed about trends of targeted industry’s
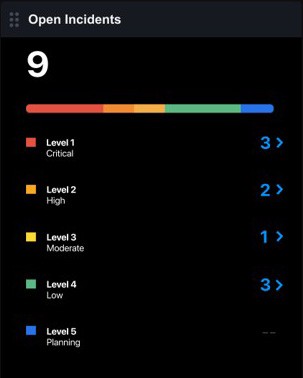
Faster Detection and Incident Response
A Starting Point For Your Investigations
Integrates With Your Security and Identity Products
Who Is The Platform For?
Designed For Cyber
Security Analysts
Intelligence Analyst
Operations Analyst
Incident Responders
Vulnerability Analyst
Chief Information Security Officer
Intelligence Analyst
Intelligence Analyst
Identify threats, assess risk, provide indications and warnings
- Define cyber threat intelligence requirements, roles and methods
- Collect, deduplicate and organize data from numerous sources
- Analyze and assess the severity of the intelligence
- Monitor threat actors, malware, IOCs, and ATT&CK activity over time
- Disseminate intelligence to stakeholders in relevant formats

intelligence
Why Analyst1?
A Superior Threat Intelligence Solution
Keep your security team ahead of the bad actors with an integrated cybersecurity defense system.
-
 Automated Collection and Processing of Intelligence
Automated Collection and Processing of Intelligence
Analyst1 employs supervised machine learning and natural language processing
to transform data into meaningful intelligence, so you can track actor profiles, malware profiles, and ATT&CK usage. -
 Vulnerabilities Linked to Threats
Vulnerabilities Linked to Threats
Identify your assets with exposure to bad actors by correlating endpoint visibility
with threat intelligence to identify assets with vulnerabilities that put you at risk -
 The Ability to Create and Deploy Defense Rules
The Ability to Create and Deploy Defense Rules
Create, test and deploy intrusion prevention and intrusion detection rules with Analyst1.
Update your sensor configurations and watchlists by prescribing and orchestrating preapproved mitigation actions.

solutions
Contact Analyst1
Interested In Our Threat Intelligence Solution?
Get in touch with our team to explore how Analyst1 can help you take control of your cybersecurity.
Threats & Trends
Your go-to source for industry news, threat intelligence trends, and all things cyber security.