
New Ransomware Turns to Disruption and Sabotage
Written by Jon DiMaggio.
On Thursday, June 10th, 2021, a discussion on a malware forum used by DarkSide, REvil, and other known ransomware gangs caught our attention. The forum is used primarily by Russian-based criminals to recruit hackers/affiliates who support and discuss ransomware operations. Unfortunately, this type of activity has become the norm, and many more significant well-known gangs have ceased posting due to the attention drawn to them following the Colonial Pipeline attacks in May of this year.
Still, many skilled and capable criminal hackers who support and conduct the attacks as affiliates for ransomware groups thrive on forums, markets and chat rooms across the internet and the Darkweb. While monitoring some of the conversations, we noted a new arrival on June 8th, 2021, appearing with an interesting alias. The post began with the new user named RyukRans, which mimics or follows the theme of Ryuk ransomware as seen below:
The thread topic caught our attention due to its name, “Ryuk .Net Ransomware Builder v1.0“. Now, keep in mind Ryuk ransomware has existed since at least 2018 and is built on code found in Hermes V2, which originated in 2017. Therefore, any “Builder” the real Ryuk developer created would unlikely be named version 1, prompting us to research further.
It is, however, essential to first note the developer, who posted the tool to Github on June 9th, 2021, says he made the tool and named it after the popular ransomware variant and did not claim it was associated with Ryuk itself. Interestingly, other criminals were upset that he would call it Ryuk, which criminals clearly respect within the forum. Another member on the forum with stature in the ransomware scene responded to the developer, “Ryuk is a trade mark, and people should not be misled. Make your locker and call it something else”. While not the purpose of this blog, the fact that other cybercriminals take offense to the unsanctioned use of the Ryuk name is interesting.
The malware’s developer stated “I named it ryuk because it behaves like a ryuk”.
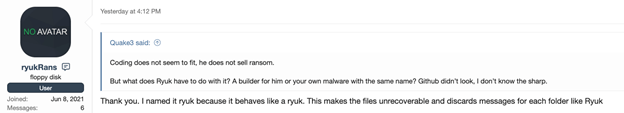
But then the developer went on to say, “This makes the files unrecoverable and discards messages for each folder like Ryuk,” and, “it does not only change extensions. It overwrites files which means nobody can ever return files back.“
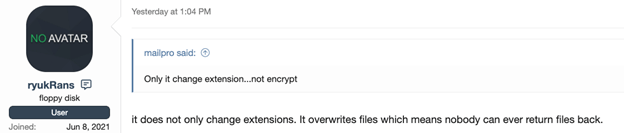
For the record, Ryuk ransomware does not destroy the victim’s files, making them unrecoverable. If it did, the attacker could not demand a ransom. However, one concerning aspect of the developer’s statements is how his ransomware functions by overwriting victim data.
This means it is not ransomware but instead a tool designed for sabotage and disruption purposes. If used in a fashion similar to traditional ransomware attacks, attackers could use the variant to destroy an organization’s entire infrastructure. It is unclear why a criminal would want to create such a tool. However, this is happening based on the discussion, and the presence of the tool on Github. Usually, we only see sabotage or destructive tools used by nation-states, but this is not the case based on the public marketing (the developer wants funding for the project) and discussion of the malware with other criminals. Anyone with a grudge or vendetta against a private sector organization could use the destructive malware to target private sector companies.
While this project is currently in its infancy, this is how larger more significant attacks begin. As they gain more attention and funding, it could develop into a much greater problem.
The ransomware scene is growing and becoming a huge issue for both government and private sector organizations. If you ever ask yourself how ransomware attacks could get worse, this is the answer. On the one hand, it seems odd there would be an interest in such a project since the attacker cannot ask for a ransom. On the other hand, as mentioned earlier, this destructive malware is perfect for an adversary that wants to disrupt operations. Consider Apple who was targeted earlier this year in a major ransomware attack. If the attacker destroyed their data instead of encrypting and stealing it, the lasting effect would be far more significant.
Much like a human virus, however, computer-based viruses or malware also have to start somewhere. Hypothetically, a government that felt its criminals would not target their own country or “motherland” could introduce such a concept and seed the idea, knowing their adversaries would likely become its first victims. While we have not completed all of our analysis at this time, this is probably a criminal effort, and there is no sign it has anything to do with a government operation. However, its destructive purpose and discussion on a forum known for seeding some of today’s most notorious ransomware attackers is troubling. We will post more information as it becomes available but we wanted to draw attention to the change in direction. This is the first time we have seen a malware developer pushing ransomware that is actually a destructive wiper promoted on ransomware forums.
At the time of this writing, this incident has been reported to both law enforcement and GitHub.


