Attribution Matters!? Eight Names of Ransomware Actors Revealed, So What?
Written by Anastasia Sentsova
Background
Starting 2021, eight names of individuals associated with LockBit and other ransomware groups were revealed to the world: Mikhail Matveev (aka boriselcin & wazawaka), Ruslan Astamirov, Mikhail Vasiliev, Artur Sungatov, Ivan Kondratyev (aka Bassterlord), Yevgeniy Polyanin, Yaroslav Vasinskyi and most recently Dmitry Khoroshev (aka LockBitSupp) who the DOJ publicly named on May 7, 2024. Three out of eight, Astamirov, Vasinskyi, and Vasiliev, were arrested. However, the remaining actors were identified as physically located in Russia and remain “at large.”
While identifying ransomware actors may initially appear significant, many, including defense contractors, question its true impact. These professionals argue that the primary focus should be strengthening data safety and implementing robust protective measures. Attribution of actors poses a significant challenge due to the complexity involved. Attackers often employ sophisticated techniques to conceal their identity and origins, complicating efforts to attribute attacks accurately. Therefore, while identifying ransomware actors may provide some degree of closure and accountability, some say its significance in combating the overall threat of ransomware may be exaggerated. Furthermore, skepticism regarding the importance of attribution arises from the realization that some identified actors reside in jurisdictions with a lack of extradition laws for citizens and limited potential for international cooperation. Therefore, allocating resources and investment in attribution efforts, which may not directly contribute to enhancing security, may not be justified.
Despite these valid points, the attribution of actors plays a crucial role in combating ransomware. Let’s explore some of the key benefits:
1. Setting a Public Example & Applying Pressure on Actors
Accountability plays a vital role in combating ransomware by holding actors responsible for their actions. Identifying attackers and publicly disclosing their identities not only raises awareness among the general public about the seriousness of cyber threats and the importance of cybersecurity but also sets a powerful example for other actors.
Exposing ransomware actors has also become a powerful tool in fighting ransomware by leveraging psychological pressure to deter future attacks. A notable example of this is the recent revelation of the identity behind the LockBitSupp persona, a prominent member of the LockBit ransomware gang. As announced, Dmitry Khoroshev, a Russian national residing in Voronezh, Russia, was identified as a key member behind LockBit operations. This revelation marked the culmination of nearly two months of law enforcement efforts, demonstrating the effectiveness of targeted attribution efforts in disrupting cybercriminal operations.
It all began with the initial announcement on February 19, 2024, when the public learned that, through the coordinated efforts of the taskforce “Operation Cronos,” led by the National Crime Agency (NCA), a UK National Law Enforcement Agency, in collaboration with the FBI, Europol, and nine other countries compromised LockBit’s infrastructure. What sets this takedown apart from previous actions against ransomware is the innovative approach adopted by law enforcement. Utilizing PsyOps (Psychological Operations), such as the intrigue surrounding the revelation of LockBitSupp’s identity or providing a subtle hint of potential cooperation of LockBit’s leader with law enforcement, demonstrates a departure from traditional methods. These psychological tactics targeted two components vital to the success of LockBit operations: brand reputation and interpersonal relationships among actors.
You can read our previous analysis here.
The revelation of LockBitSupp’s identity achieved its intended goal, sparking a significant debate on the DarkWeb forum XSS. A forum member using the moniker h1dden_pr0cess accused LockBitSupp of cooperating with law enforcement. As previously mentioned, this suggestion of possible cooperation between LockBit and law enforcement was strategically aimed at fostering distrust among forum members, which appears to have been successful.
Interestingly, h1dden_pr0cess’s account was swiftly banned from XSS minutes after posting the message. The explanation for the ban cited multiple accounts associated with drunken_master, another prominent member of XSS whose account had ironically been banned in 2022. This rapid response from the forum administrators suggests a concerted effort to maintain control and suppress discussions that may disrupt the community’s cohesion or challenge its established norms.
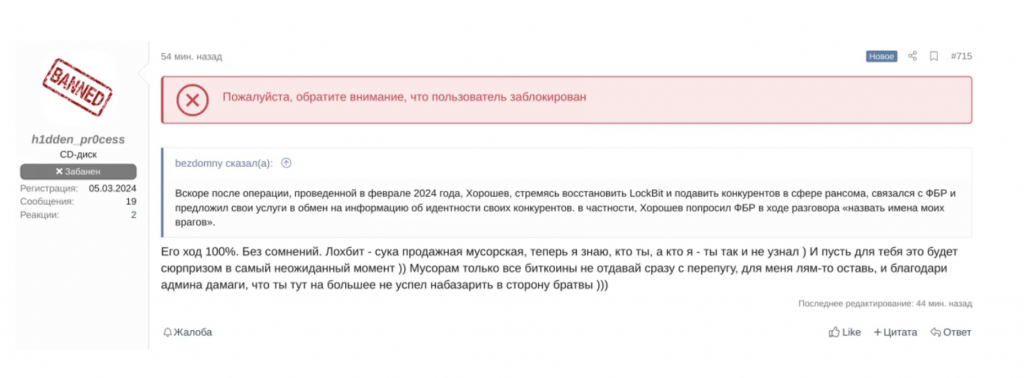
Source: XSS[.]is
The objective of generating widespread discussion in both public and underground spheres is to establish a public precedent for those currently involved in ransomware attacks or contemplating engaging in such activities. This is a potent deterrent and communicates a distinct message to prospective ransomware actors that their actions will not escape consequences.
Even though identified actors may reside in Russia and thus may not face prosecution in the US or UK due to extradition laws, they are likely to attract attention from Russian law enforcement. Given the current geopolitical landscape and ongoing socio-economic developments within Russia, including the mobilization of its citizens, the outlook for these ransomware actors appears grim. The possibility of potential cooperation with Russia, for example, also can’t be taken entirely off the table, which we will explore in our next section.
2. International Cooperation
International cooperation in combating ransomware attacks is crucial for effectively addressing this global threat. Despite its challenges, attribution efforts can potentially foster collaboration between countries in several ways including information sharing, joint investigations and facilitating legal cooperation. However, it’s crucial to acknowledge that cooperation in attributing ransomware attacks may face challenges, particularly in geopolitical tensions or conflicts.
For instance, Russia (which dominates the ransomware scene by the number of actors operating within its borders) is unlikely to cooperate at present. The prevailing geopolitical tensions and ongoing militia conflicts, including the invasion of Ukraine further exacerbate this situation. Despite the challenges, continued efforts to foster collaboration and dialogue among nations remain essential for effectively combating ransomware and safeguarding global cybersecurity. It’s worth noting that there have been instances where Russia has responded positively to calls for collaboration, highlighting the potential for future cooperation despite current obstacles.
In 2021, discussions regarding the issue of ransomware, particularly concerning the REvil syndicate, were prevalent due to its significant activity during that period. Operating from approximately December 2020 to November 2021, the actors behind the group were responsible for several high-profile attacks, including those targeting Kaseya and JSB. Throughout 2021, there was a concerted effort to crack down on REvil, resulting in arrests and sanctions against its actors. On November 8, 2021, it was announced that a 22-year-old Ukrainian national, Yaroslav Vasinskyi was responsible for multiple ransomware attacks, including the one on Kaseya, had been arrested. Vasinsky was apprehended in Poland and remained there until he was extradited to the US in March 2022.
This also led to multiple rounds of discussions between the US and Russia, including conversations between Presidents Vladimir Putin and Joseph Biden. The first face-to-face meeting between Biden and Putin occurred on June 16, 2021, in Geneva, where they discussed the ransomware problem. Subsequently, on July 9, 2021, the two presidents continued their discussions over the phone.

White House and Kremlin
Source: White House and Kremlin official websites
During cooperation between US and Russian law enforcement agencies, the US shared intelligence regarding individuals residing in Russia involved in ransomware operations. On January 14, 2022, the Federal Security Service (FSB) announced the detention of 14 individuals suspected of being behind REvil’s operations. Arrests were made across Moscow, Saint-Petersburg, Leningrad, and Lipetsk regions. As a result of the raid, authorities seized more than 426 million rubles, including cryptocurrency, 600 thousand USD, and 500 thousand euro, as well as computer equipment, cryptocurrency wallets used for illicit activities, and 20 premium-class cars purchased with funds obtained from criminal proceeds.
Notably, only eight out of the 14 claimed suspects appeared in the court. The defendants face charges related to illegal financial activities, as outlined in Part 2 of Article 187 of the Criminal Code of the Russian Federation. Two of them are also accused of developing and distributing malware, as per Part 2 of Article 273 of the Criminal Code.
Yevgeniy Polyanin likely was one such individual of interest to the US. At the time of Vasinskyi’s arrest, Polyanin, a Russian national, was charged with conspiracy to commit fraud and related activities in connection to ransomware and money laundering activities. If convicted on all counts, he faces a maximum penalty of 115 and 145 years in prison, irespectively. However, Polyanin has neither been apprehended nor convicted (at least publicly) and has not been legally held accountable for his crimes.
Mikhail Golovachuk was one of the eight REvil actors who faced charges. “Looking into the future,” he commented on his Instagram post on December 2, 2019, posing in front of the State Duma building in Moscow, Russia, located nearly 500 meters from the Kremlin. With the best intentions to serve his country, little did Golovachuk know that he would become a bargaining chip in Russia’s negotiations with the US.

Source: Instagram
Despite the US withdrawing from cooperation with Russian law enforcement due to the invasion of Ukraine, hearings are still ongoing. In early April 2024, suspected members of REvil once again appeared in court, marking over two years of legal proceedings. In a photograph captured by Russian Kommersant, six individuals were seen in the dock, with one wearing a sweatshirt bearing the words “Team Putin.” During the hearing, the defendants’ lawyers presented evidence indicating no grounds for criminally prosecuting their clients. They argued that the investigation materials, including the examination that led to the case being initiated, were compiled with violations. The fate of these individuals remains uncertain; however, given their involvement in such a publicized case, all eight are likely to be detained for an extended period, possibly until an opportunity arises for international cooperation.
Although the cooperation between Russia and the US began promisingly, it quickly stalled due to Russia’s invasion of Ukraine in February 2022. Despite the short-lived nature of this collaboration, which ended with the US withdrawal following Russia’s invasion of Ukraine, the case set a precedent as Russia’s initial significant attempt at collaboration with the US in combating ransomware.
Looking ahead, if circumstances allow for renewed cooperation between the two countries, there may be potential for joint efforts to address cyber threats, including ransomware. If such an event were to occur again, those individuals publicly known and indicted by the US would likely be the first on the list for prosecution. However, the geopolitical landscape and ongoing conflicts will undoubtedly influence the feasibility and scope of any future collaboration. Nevertheless, the initial attempt underscores the importance of international cooperation in tackling cybercrime and highlights the potential benefits of shared efforts in enhancing cybersecurity on a global scale.
3. Mapping Out Illicit Activity & Opening a Path for a New Legislation
One critical aspect of attribution of actors is identifying their geopolitical alignment, which often determines their affiliation with a specific community and state. This affiliation, in turn, influences their preferences in target selection and tactics. For example, in the case of the eight individuals whose identities were publicly revealed, we observe that they belonged to the Russian ransomware community, indicating a geopolitical alignment with Russia.
This attribution is not solely based on language or nationality; among these actors are individuals of various nationalities, including Russians, Chechens, and Ukrainians. However, the common thread is the use of the Russian language. This can be explained by the shared linguistic heritage among people historically from former Soviet Union countries, where citizens often speak and understand Russian regardless of nationality.
For example, identifying belonging to a specific community, such as the Russian ransomware community, helps us understand internal operations better. It is common for these groups to have specific lists of targets they are allowed to attack, with countries in the Commonwealth of Independent States (CIS) often excluded from these lists. Although some sectors were off the list, including the healthcare sector, for example, it is no longer the case. With the identification of geopolitical alignment, it becomes clear why such preferences have changed.
While the direct involvement of the Russian State remains unclear, actors who are geopolitically aligned with Russia may voluntarily follow its agenda. Those supportive of Russia may feel even more compelled to adhere to its objectives, often influenced by a widespread ideological campaign aimed at militarizing Russian society across various fronts, including the digital realm. This ideology dissemination fosters a sense of camaraderie and shared purpose among ransomware actors aligned with Russia’s interests. It promotes a common narrative that legitimizes their actions and fosters collaboration in pursuit of shared goals, whether financial gain or advancing geopolitical agendas.
Indeed, since the invasion of Ukraine, there has been a notable increase in attacks targeting sectors that were previously off-limits. A prime example is the recent attack on Change Healthcare by Alphv BlackCat, marking the most significant attack on the healthcare sector to date, resulting in more than a billion in financial losses. Given that BlackCat is comprised of Russian-speaking individuals who clearly align with Russia geopolitically, this incident now emerges as a matter of national security. Consequently, it underscores the imperative of proposing new legislation to counteract this escalating threat effectively.
Understanding the geopolitical landscape inhabited by ransomware actors equips law enforcement agencies and policymakers with the foresight needed to anticipate and counter cyber threats. This awareness enables targeted interventions to disrupt criminal networks and prevent future attacks.
In addition, by collecting evidence and disseminating it publicly or privately, collaboration between the public and private sectors is significantly strengthened. The exchange of information between these sectors lays the groundwork for new legislation addressing ransomware. For instance, disclosing cryptocurrency addresses crucially aids in effectively combatting this threat. Thus, policymakers can formulate targeted legislative measures to bolster cybersecurity defenses and hold ransomware actors accountable by identifying gaps in current laws and regulations. These measures may encompass enhanced data protection, stricter penalties for cybercriminals, and frameworks for international cooperation in investigations and prosecutions.
In the ongoing debate over the importance of attribution, the answer may lie in recognizing the significance of both defensive measures and attribution efforts. Effective cybersecurity strategies require a combination of proactive defense mechanisms and the identification of threat actors. By understanding the geopolitical landscape and motives of ransomware actors, along with the tactics and techniques they employ, and by promoting collaboration between the public and private sectors, stakeholders can bolster their capacity to combat evolving cyber threats effectively.



