
Why North Korea Steals Money
North Korea had a huge year in 2021, stealing nearly $400 million in cryptocurrency. This is a nearly $100 million increase from the previous year, bringing the total to $1.5 billion in cryptocurrency stolen in the past five years. North Korea is not limited to stealing cryptocurrency; they also steal from banks all over the world along with deploying ransomware to collect money for the regime. They do this to get around sanctions/UN resolutions in order to fund the regime and weapons programs.
How North Korea Steals Money
Traditional Banks
One example of North Korea stealing money from traditional banks is the $81 million Bangladesh Bank heist on February 4, 2016. Hackers used SWIFT, which stands for the Society for Worldwide Interbank Financial Telecommunications, which uses a trusted closed computer network communication between member banks around the world. The system has 11,000 users and processes about 25 million communications a day, most of them being money transfers. The hackers used compromised SWIFT credentials of Bangladesh’s central bank to send more than three dozen fraudulent money transfer requests to the Federal Reserve Bank of New York, asking to transfer millions of the Bangladesh bank’s funds to several bank accounts in Asia. $81 million was successfully transferred before an additional $850 million was halted.1
Crypto
One example of how North Korea steals cryptocurrency occurred on August 19, 2021, when cryptocurrency exchange Liquid.com announced that an unauthorized user had gained access to some of the cryptocurrency wallets managed by Liquid. The night before, 67 different ERC-20 tokens, along with large quantities of Ether and Bitcoin, were moved from these wallets to addresses controlled by a party working on behalf of DPRK. The attacker then used decentralized protocols to swap the various ERC-20 tokens for Ether. From there, they mixed the Ether, swapped the mixed Ether for Bitcoin, mixed the Bitcoin, consolidated the mixed Bitcoin into new wallets, and then deposited the funds into crypto-to-fiat exchanges based in Asia. As a result, approximately $91.35 million in crypto assets was laundered.2
Ransomware
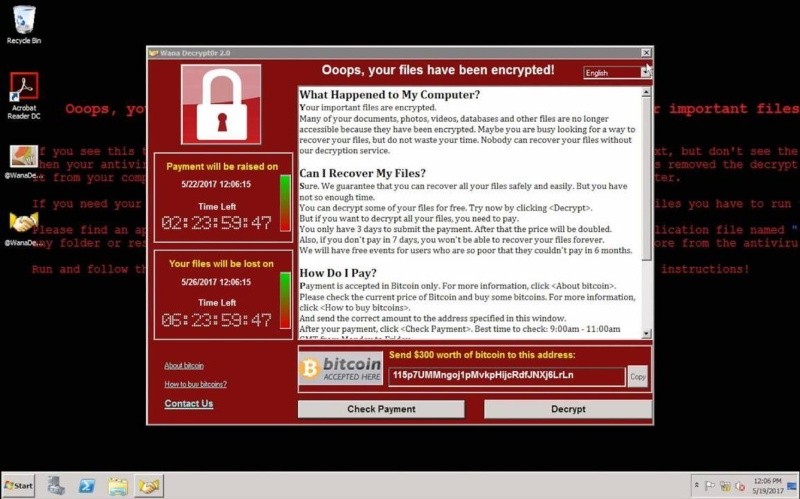
An example of North Korea distributing ransomware to generate money was the WannaCry attack in May 2017. WannaCry is ransomware that contains a worm component. It attempts to exploit vulnerabilities in the Windows SMBv1 server to remotely compromise systems, encrypt files, and spread to other hosts. WannaCry spread fast, encrypting hundreds of thousands of computers in more than 150 countries in a matter of hours. It was the first time ransomware, a malware that encrypts a user’s files and demands cryptocurrency in ransom to unlock them, had spread across the world in what looked like a coordinated cyberattack. Researchers from Symantec, a cybersecurity software company, claim that tools and infrastructure used to carry out recent WannaCry ransomware attacks show strong links to a North Korean cyber group, a group believed to be responsible for the infamous Sony Pictures hack and the $81 million theft from the Bangladesh central bank.3
How North Korea Spends the Money
Bolstering Their Nuclear Program
According to a February 2022 UN report, North Korean cyberattacks have stolen millions of dollars worth of cryptocurrency to fund the country’s missile programs. And in 2019, the UN reported that North Korea had accumulated an estimated $2 billion for its weapons of mass destruction programs by using sophisticated cyberattacks. North Korea has been banned by the UN Security Council from carrying out nuclear tests and launching ballistic missiles. However, the UN report says that despite crippling sanctions, North Korea has been able to continue developing its nuclear and ballistic missile infrastructure.4
Having a nuclear weapons program is important to North Korea. As Kim Jong-Un says, “As a responsible nuclear weapons state, our Republic will not use a nuclear weapon unless its sovereignty is encroached upon by any aggressive hostile forces with nukes, as it had already declared, and it will faithfully fulfill its obligation for non-proliferation and strive for the global denuclearization.” So far, North Korea has detonated six nuclear weapons.5

Launching Missiles
Just like the nuclear program, missiles are deemed important to the North Korean regime. During the 8th Party Congress in January, Kim Jong-Un said the development of military reconnaissance satellites and hypersonic missiles, along with unmanned attack drones, are the major goals for the next five-year plan. North Korea has released photographs, which it said were taken from its most powerful missile launch in five years. Pyongyang confirmed it had tested a Hwasong-12 intermediate-range ballistic missile (IRBM). At its full power, it can travel thousands of miles, putting areas like US territory Guam within striking distance. Depicted below is a photo North Korean officials said was taken from the Hwasong-12 IRBM. Pyongyang has conducted over 100 launches of several different types since 1998.5, 6
Leadership in Luxury
Despite having a struggling economy and international sanctions, North Korea attempts to import luxury items for the elite. In 2019, North Korea imported custom armored luxury cars worth $500,000 each. There are even two luxury stores in Pyongyang where you can buy just about anything, including premium blended whisky, jewelry, and perfume, including many items that are banned by the UN Security Council. The stores are said to be cash-only, with the profits likely going to the weapons program.
What is being done about it?
Sanctions
For years, the United States and the international community have attempted to negotiate with North Korea to end its nuclear and missile development. However, as North Korea continues to develop and test nuclear and missile weapons, the global community has responded with sanctions. Recently, as North Korean cyber actors have conducted destructive cyberattacks, along with stealing money, sanctions are continuing to cut off the country from the rest of the world. So far, the United States has sanctioned 187 entities and individuals over time, and 15 UN resolutions have been imposed, many of which are directly related to the weapons programs.5
Arrests & Indictments
On February 17, 2021, the Department of Justice announced charges against three North Korean military hackers indicted in wide-ranging schemes to commit cyberattacks and financial crimes across the globe. The three are charged with participating in a criminal conspiracy to conduct a series of destructive cyberattacks to steal and extort more than $1.3 billion from cryptocurrency and financial institutions. According to the FBI, “Today’s unsealed indictment expands upon the FBI’s 2018 charges for the unprecedented cyberattacks conducted by the North Korean regime.”7
On March 22, 2021, the Department of Justice announced that after nearly two years of legal proceedings, a North Korean national was extradited to the United States. This was the first time ever that a North Korean national was extradited to the United States. Mun Chol Myong is accused of laundering money through the US financial system and deceiving US banks to get around sanctions and provide luxury items to the North Korean regime.8
Awareness & Cybersecurity
Along with arrests, indictments, sanctions, and UN resolutions, the United States continues to put various FBI/CISA cybersecurity awareness reports on North Korean cyber-related activities. Joint Alert (AA21-048A), released on February 17, 2021, is an analysis of North Korea’s cryptocurrency malware AppleJeus.
The alert includes the activity of North Korean cyber actors that have targeted organizations for cryptocurrency theft in over 30 countries, along with the indicators of compromise used to facilitate the thefts. The alert also includes proactive mitigations for defense against AppleJeus malware and mitigation if the malware is identified within a network. A second CISA report released in February 2021 is Security Tip (ST18-002), which gives information about defending against illicit cryptocurrency mining activity, including cybersecurity best practices that can help protect internet-connected systems and devices.
Recently, the United States said it would consider proactively disrupting cyber criminals’ operations even if doing so may impede the state’s ability to arrest and indict the alleged perpetrators.9
What to expect in the future?
Until the cryptocurrency industry figures out how to secure itself against hackers or prevent it from being laundered, North Korean hackers will continue to steal to fund the regime. The cryptocurrency and banks will need federal help to slow down the movement of stolen funds and take opportunities to freeze or seize the assets and hold the actors accountable. “The North Korean regime has figured out they don’t have any other options. They don’t have any other real way of engaging with the world or with the economy. But they do have this pretty awesome cyber capability,” says Fred Plan of Mandiant. “And they’re able to leverage it to bring money into the country.”
Sources:
- https://www.wired.com/2016/05/insane-81m-bangladesh-bank-heist-heres-know/
- https://www.justice.gov/opa/pr/three-north-korean-military-hackers-indicted-wide-ranging-scheme-commit-cyberattacks-and
- https://www.techtimes.com/articles/208029/20170523/wannacry-ransomware-highly-likely-carried-out-by-north-korean-hacker-group-symantec-says.htm
- https://www.justice.gov/opa/pr/first-north-korean-national-brought-united-states-stand-trial-money-laundering-offenses
- https://blog.chainalysis.com/reports/north-korean-hackers-have-prolific-year-as-their-total-unlaundered-cryptocurrency-holdings-reach-all-time-high/
- https://www.bbc.com/news/world-asia-60281129
- https://www.everycrsreport.com/reports/R46349.html
- https://www.bbc.com/news/world-asia-60193714
- US pledges to take a ‘hands-on’ approach to disrupting cyber criminals | IT PRO


