
The Rise and Rebranding of Ransomware in 2021
Ransomware attackers dominated headlines in 2021 targeting larger organizations with even bigger ransom requests catching attention of both law enforcement and CISA. With an administration vocally committed to stopping ransomware in its tracks, FBI and CISA revved up alerts to aid industry in understanding ransomware threat group behaviors, targets and key attack vectors.
In this piece, we will review which ransomware attacks brought on FBI and CISA alerts, how the ransomware threat landscape has changed in terms of targets and if drawing the attention from FBI/CISA forced certain groups to disappear or rebrand.
Russia’s Cybercrime Track Record
The cybercriminal groups behind many of the ransomware attacks in 2021 are physically located in Russia. While the cybercriminal groups are primarily attacking and deploying ransomware for profit, the change in targets from previous years does fit Russian government cyber targets. According to Jon DiMaggio with Analyst1 and his paper Absolute Ransom: Nation-State Ransomware, there are traceable links from the Russian government to ransomware criminal groups acting against the U.S.
The use of cyber for attacking critical infrastructure and supply chains isn’t new for Russia. In 2008, Russia attacked Georgia’s government, media sites, and a gas pipeline. Russia’s cyberattacks against Ukraine have occurred since at least 2010, and include hacking of Ukrainian government systems and attempted disruption of a presidential election. One Russian hacking group, Sandworm, is reported to be behind the malware that was used to attack the Ukrainian power grid, which left more than 200 thousand people without power, as well as an attack on a mining company and a railway operator.
The path to a ransomware fueled 2021 against the U.S. was quite predictable given Russia’s previous behaviors. The biggest difference? This year, they figured out how to truly monetize the attack vector and disrupt key operations forcing victims to pay.
Notable Ransomware Attacks of 2021
- April 2021: The attack on Colonial Pipeline is arguably one of the highest profile ransomware attacks of 2021 in the United States. Over 100 gigabytes of internal information was stolen and threatened to be released publicly. Colonial Pipeline paid the $5 million dollar ransom within hours. However, recovery was slow after a 6-day pipeline shutdown. The attack by DarkSide crippled the pipeline that delivers nearly 50% of the fuel to the East Coast.
– FBI and CISA released Alert AA21-131A, DarkSide Ransomware: Best Practices for Preventing Business Disruption from Ransomware Attacks. The Alert includes not only the summary of what occurred but mentions the technical details, mitigations, further resources available, along with updates that include associated IOCs and a malware analysis report.
- Memorial Day 2021: JBS Foods, the largest beef supplier in the world had its meat production interrupted in the U.S. and Australia from a ransomware attack. JBS made the decision to pay the ransomware group REvil $11 million to minimize the impact to the food supply chains.
- Fourth of July 2021 Weekend: Kaseya, a Managed Service Provider (MSP), was attacked by REvil. REvil used one of Kaseya’s own tools, VSA, which is used by IT professionals to manage servers, desktops, and other network devices, to infect up to 1,500 clients of Kaseya with REvil ransomware.
– After the attack the FBI and CISA responded with guidance for incident response, Kaseya Ransomware Attack: Guidance for Affected MSPs and their Customers that includes ransomware best practices, general mitigations, and hardening guidance for MSPs and customers. On July 3rd after the attack on Kaseya, President Joe Biden said he had ordered U.S. Intelligence agencies to investigate the recent REvil ransomware campaign that affected several organizations using the Kaseya VSA platform. The FBI was able to access the servers of REvil and obtain the decryption keys to the ransomware. The FBI did not release the keys immediately so that REvil would not be tipped off as they prepared to launch an attack on REvil’s infrastructure. The decryption keys were eventually released and turned into a universal decryptor in September 2021 allowing over 250 REvil victims to use the decryptor.
- August 2021: After observing an increase of high impact ransomware attacks, the FBI and CISA released Alert AA21-243A, Ransomware Awareness for Holidays and Weekends. Several recent attacks had occurred during holiday weekends, including Mother’s Day, Memorial Day, and Fourth of July when offices are minimally staffed or completely closed. The FBI and CISA suggest organizations engage in preemptive threat hunting on their networks to search for signs of threat actor activity to prevent attacks before they occur or to minimize damage in the event of a successful attack. The FBI and CISA strongly discourage paying a ransom to criminal actors. Payment does not guarantee files will be recovered, nor does it ensure protection from future breaches. Payment may also embolden adversaries to target additional organizations, encourage other criminal actors to engage in the distribution of malware, and/or fund illicit activities.
- September 20, 2021: NEW Cooperative Inc. publicly stated that it had been hit by BlackMatter ransomware. The attack locked up the computers used to manage animal feeding schedules along with food supply chains that include 40% of the nation’s grain production.
– About one month later joint Cybersecurity Advisory AA21-291A was produced by CISA, FBI, and the NSA to provide information on the BlackMatter ransomware. The Advisory mentioned how BlackMatter is the likely rebrand of DarkSide that disappeared after the attack on the Colonial Pipeline.
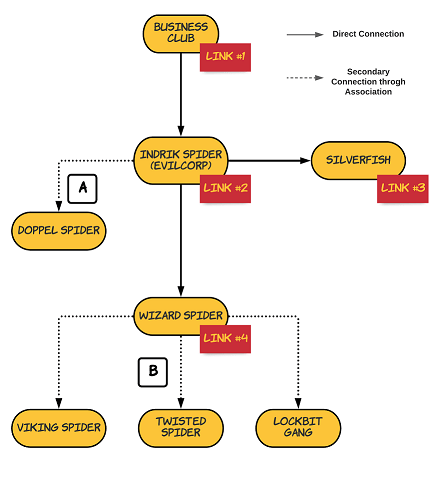
Groups that Went Under or Rebranded
All the high-profile ransomware attacks on U.S. critical infrastructure and supply chain started to draw the attention of the U.S. federal government. This extra attention has caused some of the ransomware groups to disappear voluntarily/involuntarily or rebrand themselves in an attempt to evade the attention.
In early November 2021 multiple news outlets reported that the BlackMatter group announced plans to shut down operations in a message posted to its portal, “Due to certain unsolvable circumstances associated with pressure from authorities (part of the team is no longer available, after the latest news) — project is closed.” The message follows a recent New York Times report that announced that the U.S. and Russia had started collaborating more closely to crack down on cybercriminal organizations. The shutdown also came after the joint alert from CISA, FBI, and NSA that the group had targeted multiple organizations considered to be critical infrastructure.
Shortly after President Joe Biden ordered U.S. intelligence agencies to investigate REvil, the REvil infrastructure went offline on July 13, 2021 after law enforcement and intelligence cyber specialists hacked REvil’s computer network infrastructure and took control of at least some of their servers. REvil stayed down for a couple of months until they reemerged on the dark web in early September 2021, only to be forced offline again by a multi-country operation in October 2021.
Analysis on Impact of Law Enforcement Involvement
One of the largest impacts law enforcement has made is the arrests of individuals associated with conducting ransomware attacks. Europol at the end of October announced twelve individuals had been targeted for arrest as a result of law enforcement operating in eight countries including the U.S.
- October 26, 2021: Arrests took place in Ukraine and Switzerland.
- November 8, 2021: The Department of Justice announced a Ukrainian was arrested and charged with the REvil ransomware attack on Kaseya, along with the seizure of over $6 million in funds traced from ransom payments.
- November 2021: The State Department has offered multiple rewards for information on ransomware members: $10 million for information on key leaders of the group responsible for the attack on the Colonial Pipeline, $5 million for information leading to an arrest of any DarkSide affiliates, and $10 million for information on primary members of the REvil ransomware.
In addition to arrests, the FBI released a Public Service Announcement titled, Ransomware Victims Urged to Report Infections to Federal Law Enforcement. In it, the FBI urges victims to report ransomware incidents to federal law enforcement to help gain a more comprehensive view of the current threat and its impact on U.S. victims. The Joint Alerts bring in higher public awareness of the threat of ransomware, which hopes to increase the industry’s use of basic cyber hygiene practices to mitigate the risk of a ransomware attack.
Attention and Predictions for 2022
In 2021 the U.S. saw several high-profile ransomware attacks against critical infrastructure and supply chain companies. Many of the attacks were followed up with alerts, disruption of the groups by law enforcement with arrests and infrastructure takedowns. The groups are going to continue in 2022 with ransomware attacks to make money. Instead of going after the high-profile attacks since the activity brings unwanted attention from the federal government, they will likely target smaller companies that will allow them to stay under the radar of the federal government. Ransomware attacks will continue as long as they are profitable or until the core group of individuals that take safe haven in Russia are taken down or disrupted.


