
Lies from the DarkSide: Ransomware Gang Lied About Pipeline Attack
Written by Jon DiMaggio. 14 May 2021
In May 2021, DarkSide, a Russian criminal gang, hacked Colonial Pipeline, the organization responsible for the largest Gas pipeline spanning the east coast of the United States. However, the gang soon backtracked, claiming they did not intentionally hack the organization. Instead they claimed it was an accidental infection caused by the gang’s partner affiliate, who assisted in the attack for a share of the ransom profit.
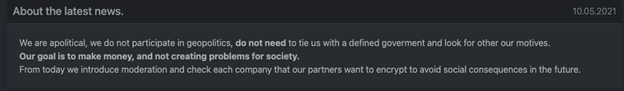
“From today we introduce moderation and check each company that our partners want to encrypt to avoid social consequences in the future.”
DarkSide Ransomware Gang
However, their statement is not valid. DarkSide predetermines and selects every target before an attack and creates individual ransomware payloads for each. The payload infects and encrypts victim data and generates the ransom note. Each ransom note is tailored to the specific victim and includes a unique key and URL as seen in Figure 1.
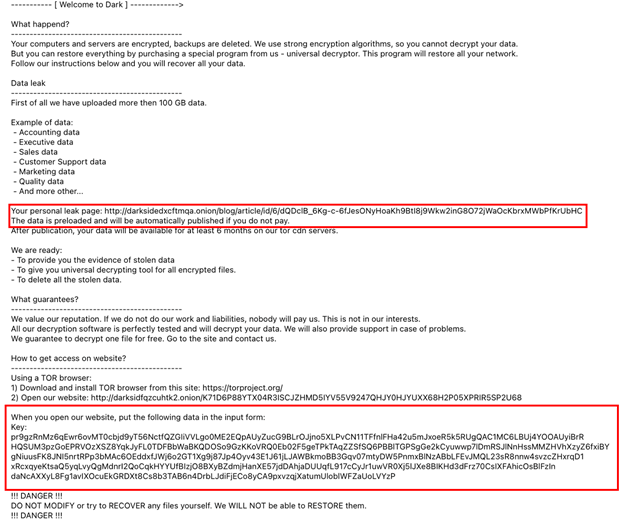
With the key, URL and payload compiled before the attack, DarkSide had to be aware of who they were attacking prior to attack execution. This is also a major attack locking down an entire network of operational systems and not some accidental infection of a few computers. Even without the evidence presented, it’s hard to fathom an attack of this magnitude could be conducted accidentally.
Without the unique key and URL, negotiations cannot begin. Using a key prevents researchers or the media from establishing communications or pretending to be the victim in an attempt to extract information from the attacker. Prepopulating a key into each ransom note and payload indicates the attacker has to select the victim intentionally. Therefore, the DarkSide group itself, not the affiliates, are responsible for the ransomware payload. DarkSide had to create the payload for the Pipeline victim specifically.
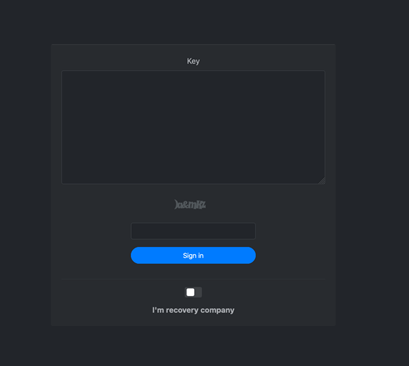
Figure 2 below shows the key authentication window presented after the victim clicks on the unique URL included in their ransom note.
Pre-Populated Data Posts
Another unique tactic used by DarkSide is how they populate victim data and messages to their data leak site. According to the ransom note, “The data is preloaded and will be automatically published if you do not pay.” DarkSide pre-loads victim data after theft to populate their data leak site once a predetermined time passes. If the victim pays, DarkSide halts the process. If not, it automatically releases a post leaking victim data. This, however, did not happen with the Colonial Pipeline attack. The attacker likely decided not to post data due to the backlash from the US government after the attack took place. The attacker may want to leave themselves plausible deniability due to the amount of attention the attack generated.
Activity Decline
The volume of victim data leak posts significantly reduced in May 2021. It’s worth noting at the time of this writing: there have only been twelve days in May to compare against other months. However, the DarkSide attacker has only made one post to their data leak site in May. In comparison, within the first twelve days of April, DarkSide made eight posts, releasing small amounts of victim data. Similarly, DarkSide made a much higher volume of posts from January through March as seen in Figure 3 below.
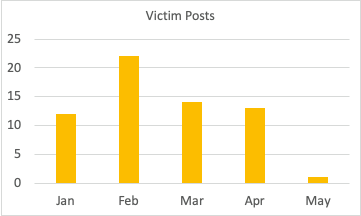
The DarkSide gang also “pinned” two older victim posts to the top of their victim list in May after the Pipeline attack took place. Yet, Darkside has still not posted any of the Pipeline data. The discrepancy may be an attempt to give the appearance operations are continuing as usual.
Additionally, due to the post DarkSide made to their website about the attack, many media outlets and researchers question whether DarkSide and the Russian government are affiliated with one another. The DarkSide gang insinuates they have no Russian government affiliation in a post they made to their website’s press section on May 10th. The message is displayed in Figure 4 below.
On 13 May, fuel once again began to flow through the pipeline delivering gas across the east coast. As Colonial reinstated pipeline operations, President Biden released an executive order addressing new SOAR cyber security requirements and standards intended to improve the security posture of federal government computer networks and systems. While all of this took place, DarkSide’s infrastructure mysteriously went down. Sometimes adversaries move their infrastructure; however, this does not appear to be the case. Instead, DarkSide’s data leak site no longer resolves. It’s unclear what happened, but a US government takedown operation is certainly plausible.
Closing
Despite the attempt to distance themselves from the Russian government, it’s worth noting the aftereffect of the Pipeline disruption fits nicely with Russian tactics used in the past (e.e., attacks against Ukraine, Georgia, Estonia, etc.). This type of attack causes major gas outages resulting in panic and doubt regarding the victim government’s ability to protect critical infrastructure. All of this fits the Russian government’s playbook of cyber operations. For now, we must treat this as a criminal attack as more evidence is needed to make any government-affiliated attribution. However, even if criminals are the only perpetrator, the claim the attack is accidental, is laughable and simply not true.
Indicators of Compromise (IOCs)
9cee5522a7ca2bfca7cd3d9daba23e9a30deb6205f56c12045839075f7627297 4098b54c9d27b00ce34d04ffac24213ed28993a2854827851b157d63407c2e4e 973dfafc3051d8c2849f62c556ab8057da706f15d1ffd8871de894ae3a24d86b 6057380a9a613b3c2b8a2f68b3bd8096e05adfc2523f5117c4112b19d4848c6d 68872cc22fbdf0c2f69c32ac878ba9a7b7cf61fe5dd0e3da200131b8b23438e7 0a0c225f0e5ee941a79f2b7701f1285e4975a2859eb4d025d96d9e366e81abb9 1d4c0b32aea68056755daf70689699200ffa09688495ccd65a0907cade18bd2a 1667e1635736f2b2ba9727457f995a67201ddcd818496c9296713ffa18e17a43 78782fd324bc98a57274bd3fff8f756217c011484ebf6b614060115a699ee134 516664139b0ddd044397a56482d7308d87c213c320a3151ccb9738e8f932654b d43b271fb4931263f8fa54b297e3cf60762a0fe5c50ed76999f276dcc3c283be 6836ec8588b8049bcd57cd920b7a75f1e206e5e8bb316927784afadb634ea4d8 3dabd40d564cf8a8163432abc38768b0a7d45f0fc1970d802dc33b9109feb6a6 ac092962654b46a670b030026d07f5b8161cecd2abd6eece52b7892965aa521b e0c0cbc50a9ed4d01a176497c8dba913cbbba515ea701a67ef00dcb7c8a84368 b6855793aebdd821a7f368585335cb132a043d30cb1f8dccceb5d2127ed4b9a4 0839aabe5fd63b16844a27b3c586c02a044d119010a1a40ee4035501c34eae0d 1ef8db7e8bd3aaba8b1cef96cd52fde587871571b1719c5d40f9a9c98dd26f84 12ee27f56ec8a2a3eb2fe69179be3f7a7193ce2b92963ad33356ed299f7ed975 fb76b4a667c6d790c39fcc93a3aac8cd2a224f0eb9ece4ecfd7825f606c2a8b6 1cc7c198a8a2c935fd6f07970479e544f5b35a8eb3173de0305ebdf76a0988cb 243dff06fc80a049f4fb37292f8b8def0fce29768f345c88ee10699e22b0ae60 508dd6f7ed6c143cf5e1ed6a4051dd8ee7b5bf4b7f55e0704d21ba785f2d5add 8cfd28911878af048fb96b6cc0b9da770542576d5c2b20b193c3cfc4bde4d3bc 27214dcb04310040c38f8d6a65fe03c14b18d4171390da271855fdd02e06768f 533672da9d276012ebab3ce9f4cd09a7f537f65c6e4b63d43f0c1697e2f5e48d bfb31c96f9e6285f5bb60433f2e45898b8a7183a2591157dc1d766be16c29893 ec368752c2cf3b23efbfa5705f9e582fc9d6766435a7b8eea8ef045082c6fbce cc54647e8c3fe7b701d78a6fa072c52641ac11d395a6d2ffaf05f38f53112556 124e83f0812629fbc7ee0330002d7e5026b0f79e29a7d42facd62dd67b83549a bc32a2ccf158ebe2b76646be865a4c6dd91da6b8e5bb0dd9520102a9bfea5439 6931b124d38d52bd7cdef48121fda457d407b63b59bb4e6ead4ce548f4bbb971 e99613d7a57a80ea3ec27c8aa8dbb37a6d80f2adeb7f02ede03c7861bd448f16 156335b95ba216456f1ac0894b7b9d6ad95404ac7df447940f21646ca0090673 94a0282c59ff9dd3528594518acc6343ec879ca394d714b23dde6e6a7d3d6e5c bac7f1cb70a0fe909590f7b270248705d216b4abaf4e5dd4969fa4f1949badec 05459376bbe170c277739cab4e425530aff0a15616297b63f0ad665c3ce0f18a 2dcac9f48c3989619e0abd200beaae901852f751c239006886ac3ec56d89e3ef bec319df9d915b37f1a9713b5ad6bad63582474fa968177fbf0bb45926b8a8c8 a11cc5051e3a88428db495f6d8e4b6381a1cb3fa5946a525ef5c00bfcb44e210 56e7b9c4b8962b6ff0d1e0162ca8515a07b576cd47ba90221354838733f8689a securebestapp20.com baroquetees.com 188.119.112.169 176.103.62.217 99.83.154.118


