
A Behind the Scenes Look into Investigating Conti Leaks
Written by Jon DiMaggio. 21 March 2022
Hello fellow “bad guy” chasers! Jon DiMaggio here! Today I wanted to discuss the Conti ransomware gang and what I learned over the past couple of weeks since their operation was exposed. When news of the Conti leak began to emerge, I felt like a child on Christmas morning, knowing today was the day I got to peel off the wrapping paper, open the box, and see all the toys that hide within. Unfortunately for me, thousands of other kids (researchers) were also opening my same present and playing with my shiny new toy! Since there are high volumes of analysis and reporting surrounding the leak, I will try not to waste your time regurgitating the same content many of my hard-working peers are reporting.
If you have read any of my previous research, you know I like to write formal investigative papers on the longer-term research I do at Analyst1. However, today I want to share some of our findings on last week’s data leak regarding the Conti ransomware operation and share how I use Analyst1, our threat intelligence platform, to explore the data released in the leak. In other words, I intend to share my findings and tell you about how I used our TIP in a non-traditional way to explore the data provided in the Conti leak. However, I promise we will share some interesting information about the leaks and explore some leads generated through our analysis to learn more about the Conti ransomware operation. To begin, let’s briefly discuss background information on the Conti ransomware gang.
Background
Conti is a Ransomware as a service provider (RaaS) that relies on hackers for hire, known as affiliates, to conduct attacks. Understand that most RaaS providers, aka the “core gang” reside in Russia. The affiliates, however, are spread across several countries but primarily live in Russia and Ukraine. Due to this, In February 2022, when the Russian government began its military invasion into Ukraine, many of us in the cyber security community questioned how it would affect the internal working relationships between the core gang and affiliates and their operations.
On the one hand, bad guys running the gangs could quietly keep their opinions and let the business operate as usual. Alternatively, they could choose sides and loudly drive their national patriotism down the throats of their fellow criminal business partners. When it comes to money and running a business, even an illegal one, I feel the correct approach is common sense, right? Well, for Conti leadership, it was not. Instead, Conti chose the latter of the two options. On February 25th, Conti posted the below message to their name and shame data leak site, Conti[.]news.
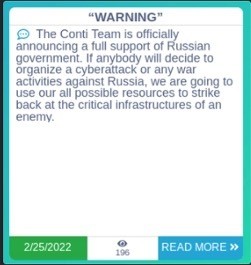
After the post, it appears Conti realized its stance might be detrimental to business and attempted to backtrack by replacing the original post with the message below:
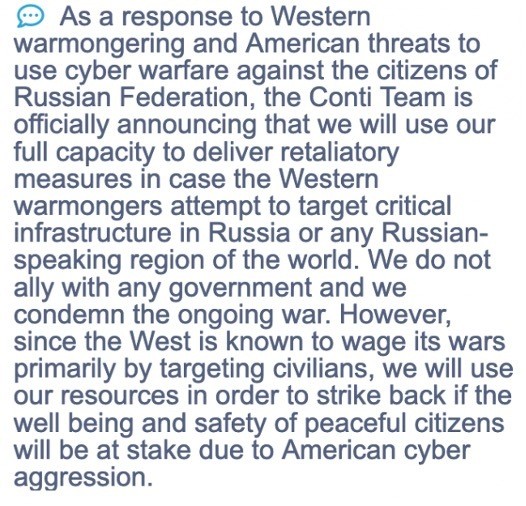
Conti, thanks for clearing that up. While slightly less polarizing than the first post, clearly, the gang chose to side with Russa publicly and is ready to attack “Western warmongers.” Since Ukraine is the region west of Russia, the statement alienates much of the gang’s affiliate resources and now makes them a target to any pro-Ukraine hacker. Additionally, Conti likely made enemies with some of the best hackers in the world, their affiliates.
Shortly after, on February 27th, 2022, an unknown person registered the Twitter handle “@ContiLeaks” and began to release private Conti data, publicly. You can see their profile below:
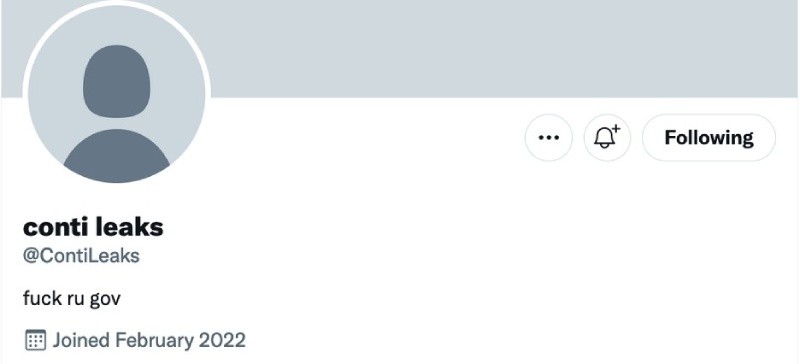
There has been a lot of chatter about who is behind the @contileak account. Some believe it is a cyber security researcher, while others believe it is one of Conti’s affiliate gang members. We don’t know which theory is correct, but one thing is clear, the leaker sides with Ukraine and is anti-Russian. But, more importantly, the leaker appears to have a serious issue with the Conti gang.
The leaker posted anti-Russian messages over the first days of activity and provided several URLs that host the Conti gang’s internal communications and other sensitive content.
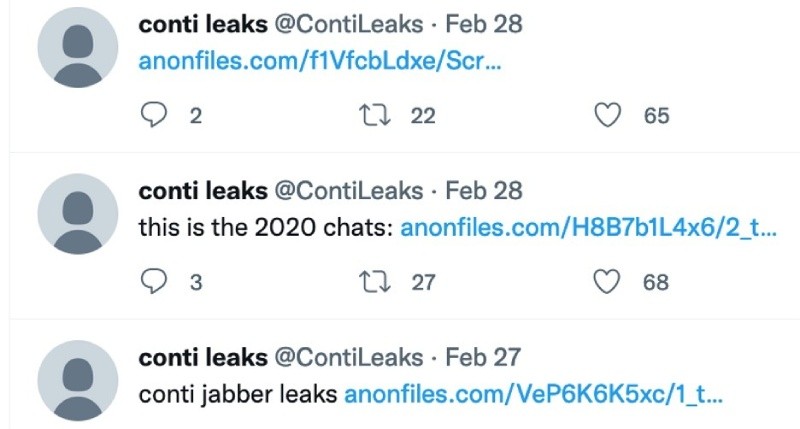
Note: Not long after posting the messages, the links to download files were deactivated by anonfiles. Fortunately, our friends at VX-Underground hosted the files on their own infrastructure, making it available for researchers to access and continue analysis. Thank you @vxunderground! You can find the files here: https://share.vx-underground.org/Conti/
Now keep in mind Conti is known for being one of the most successful ransomware attackers we have seen to date. However, based on how the gang handled the leak, we learned that the Conti gang themselves are not that bright. For example, despite the initial data leaks over the 27th and 28th, the gang could not identify how the leak occurred or prevent further exposure. Further, Conti did not secure its access from the leaker. Over the first week of March, after the initial posts from late February, the ContiLeaks account continued to post new, “fresh” leaks showing the attacker’s continued conversations.
Like a fly on the wall…
Similar to many other researchers, I spent most of that week reading through Conti’s private chat logs between its members. Understand, these chat logs captured conversations between members at all levels and ranks within the gang. However, all its members used anonymous handles associated with the gang’s Tor-based jabber server “@q3mcco35auwcstmt.onion”. While we could not distinguish the actual identity of most users within the chat logs, the conversations themselves still proved extremely valuable in learning about the day-to-day operations of the gang.
It was comical to read their “water cooler talk” as they tried to determine who leaked the information and how? However, it baffles me why Conti waited to shut down their servers after realizing someone jeopardized their entire operation. Further, why would they continue to use the compromised infrastructure for nearly a week after its exposure? Conti now understands how their victims feel when making tough decisions that impact business after a breach. Further, it is puzzling why Conti did not use a chat client that provided end-to-end encryption. If they had, the majority of the leaked data would be worthless.
On a side note, you have to love the irony. In ALL their attacks, Conti taunts its victims threatening to publish their sensitive data, making it public, which is exactly what @ContiLeaks did to them. Below is an exert from the ransom note Conti leaves on its victim’s systems after infection:

You know what they say about Karma. Now, @ContiLeaks gave the ransomware gang some of its own medicine. Thank you @ContiLeaks!
Digging through leak data
Since the names and addresses used by Conti members to communicate on their jabber server are not very useful by themselves, we needed to identify which accounts were significant and which were not. My initial approach was to map out the conversations visually, but I did not have a solution to do so quickly. So instead, after discussing with one of my colleagues, I decided to ingest the data into our Analyst1 threat intelligence platform (TIP).
Initially, I was unsure how useful it would be to analyze jabber-based chat logs since defenders primarily use threat intelligence platforms to analyze threat data. However, doing so allowed me to see the volume of messages sent from each account as well as extract domains, IP addresses, and URLs, amongst others, found in the chat logs. The below screenshot displays the most active accounts located within the chat logs. The number listed under the evidence column represents how many conversations each account posted seen within the leaked data I uploaded for analysis:
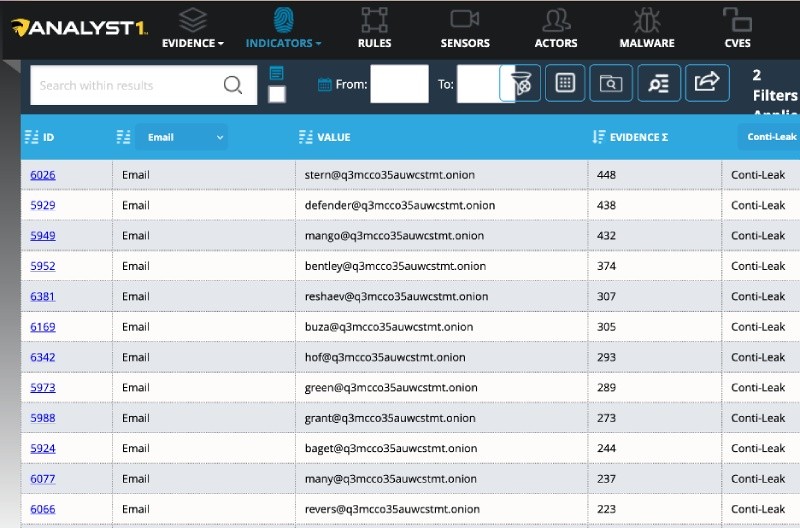
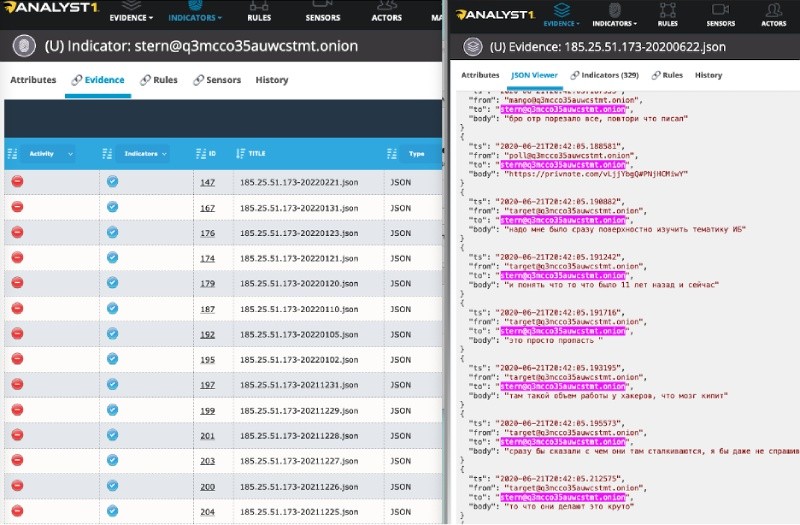
Identifying the most active accounts allowed me to focus my time and resources on a much smaller data set. Now I could focus on what I considered high-value data and return later to review the rest. For example, from the leaked data I am analyzing, you can see that the account using the handle “stern” is the most active. Examining the evidence section also shows me each JSON file the account and its associated conversation appear in. Then, when selected, the Analyst1 platform shows me exactly where the indicator or handle is used, allowing me to read the conversations between the selected target and associated Conti member as seen below.
Next, I wanted to try and pivot from the internal anonymized Conti accounts within the chat logs and find external leads. If I could find other accounts in the public domain and link it to the individual using the internal Conti handle, I thought I might be able to learn more about the operation itself or the people behind it.
To start, I wanted to try and find any conversations discussing handles or hacking forums on the dark web. Historically, ransomware bad guys spend time and communicate on dark web forums and marketplaces. They use the markets/forums to recruit hackers, obtain exploits and purchase attack resources. Therefore, I thought this was an excellent place to start since most of the leaked chat logs contain commentary about attack operations, making it likely they would discuss the forums they recruit from.
Looking for this information manually would be a tedious task. So instead, I used Analyst1 to identify accounts related to some known forums that ransomware bad guys frequent. To begin, I simply searched for any email address, URL, or domain that ended in “.onion”, the top-level domain used for ToR based websites. Then I removed results ending in “q3mcco35auwcstmt.onion” since the domain is only used for Conti’s internal chats and is not associated with external related accounts. Within the results, I found several URLs of forums I know ransomware bad guys frequent, the XSS and Exploit dark web forums. Below is an example of the data I found:
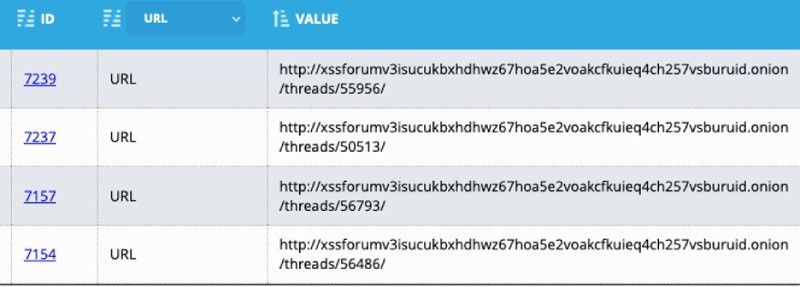
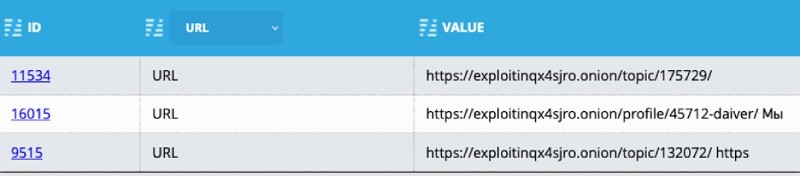
Next, I began to research the content on the associated URLs. Before navigating to the forums directly, I first looked at the associated evidence in Analyst1 to view the conversations in which the URLs are discussed. For example, the below conversation took place on September 9th, 2020 between two Conti members discussing a recruitment post on the hacking forum XSS:
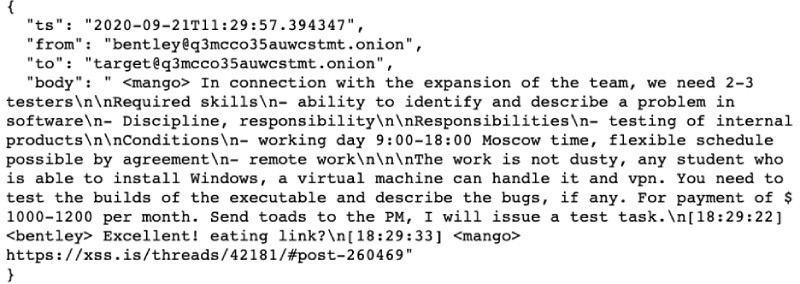
Navigating to the forum, I saw the job posted presumably by “Target”, using the alias “Khano” from their XSS account (Great Avatar, BTW!)
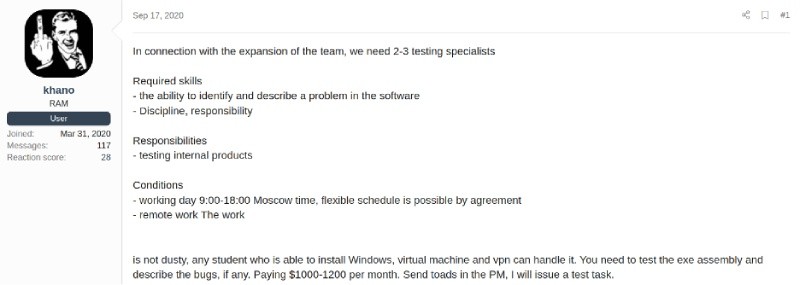
Next, I Followed Khano’s posts over time. Reading each post led to discovering several other employment and service ads posted between September 2020 through February 2021, such as the ones below that provide additional context on the labor, services and technologies Conti desired to support their operation:
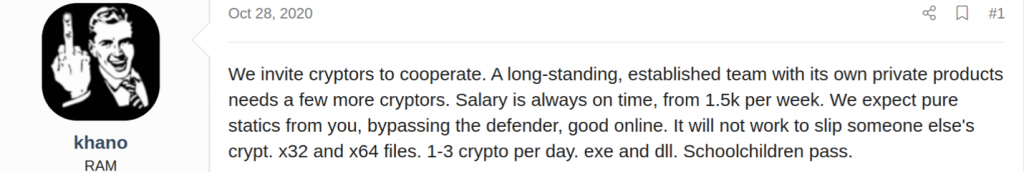
Interestingly, Conti first offered $1,000/1,200 per month in September but increased the salary offered to $1,500 per week in October. Perhaps, they were not getting the applicants they desired, so they increased the salary to lure better prospects. However, for a gang that brings in hundreds of millions in extra revenue, $1,500 per week seems pretty cheap. In the same post, Target/Khano ask for individuals with the skill to bypass (Windows) defender and use their (Conti) ransomware to encrypt files. Khano makes it clear he/she is not searching for other providers who use their own ransom payload, but only wants talent that can work with their (Conti) ransomware.
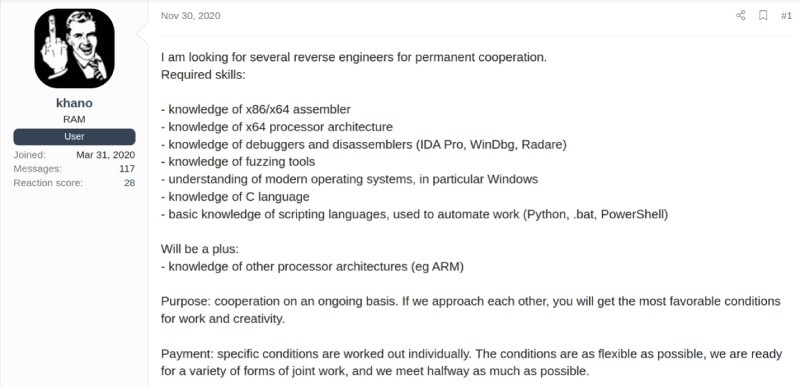
Then in February 2021, Conti is looking for bots and individuals with experience exploiting RDP, VNC, and VPN technologies to gain access into target environments. All of which are standard methods seen used in Conti attacks.

Following forum posts and ads on the Dark Web is an excellent source of information and a resource I always take advantage of when investigating cybercriminals. After reviewing the posts on XSS I jump back to the Analyst1 platform and query for email accounts for (@exploit.im) the other dark web forum I saw discussed in the leak data.
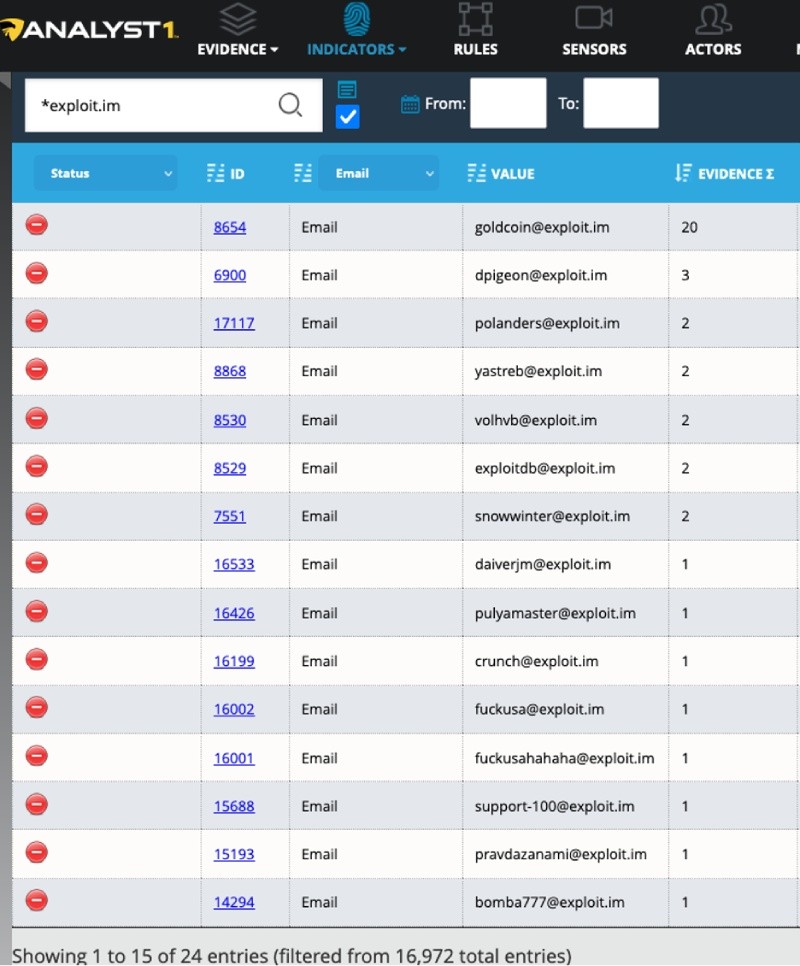
From the leaked data, 24 accounts associated with the Exploit forum exist. Using the information, I begin to go through the forum and look at each account, their posts, and mentions from other users. I found several accounts used to buy and sell digital certificates used later in malicious attacks. Below is one of the certificate related posts of interest to Conti:
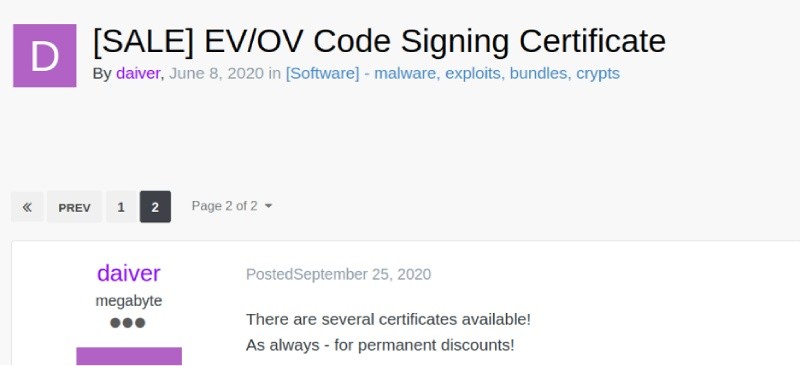
Obtaining code signing certificates makes sense since Conti needs to sign their code and malware payload so it appears legitimate and passes security checks when introducing it to victim operating systems.
Next, I continued to check the ToR based URLs and accounts discussed in the leak data. We will not detail everything we found, but one more is worth discussing. One of the accounts Conti members discuss has long-standing roots in the ransomware community. The associated Exploit account existed long before Conti ransomware operations began. The account authored a post back in 2017 that provided a hands-on tutorial on how to “write ransomware for windows” and created a tutorial with screenshots, the ransomware code itself, and even a video:
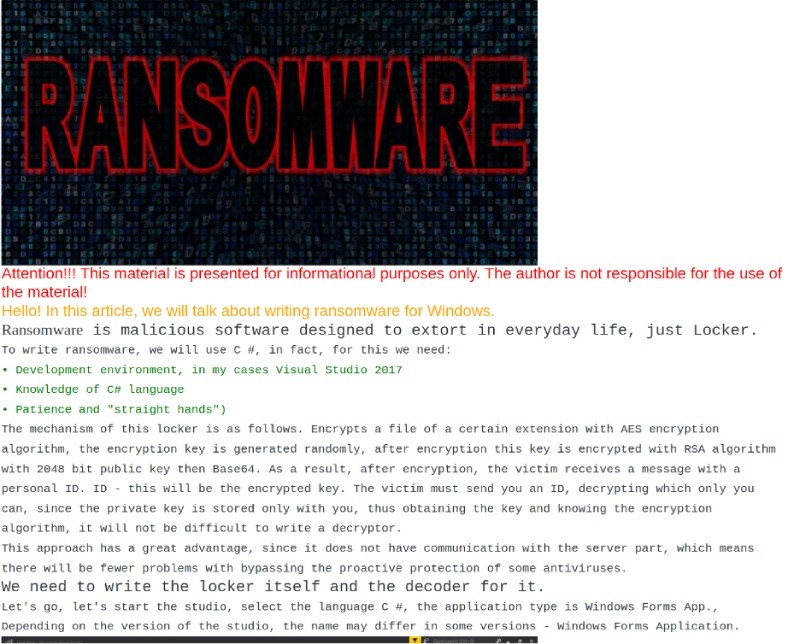
Obviously, we wanted to look for any indication the code could have later been used to create the Conti payload. Unfortunately, it was a long shot and did not match Conti ransomware code. Instead, the code appears to compile legacy ransomware detected as ransom.spora (Malwarebytes). Still, it provided us insight into the individuals working the Conti operation today and how they may have begun their interest in ransomware development years before the Conti operation began.
Since there are many valuable and interesting resources on the darkweb besides criminal forums, I looked into other URLs discussed within the chat logs. I expanded my search to show all dark web infrastructure. Analyst1 quickly identified 43 URLs accessed across 5 root domains:
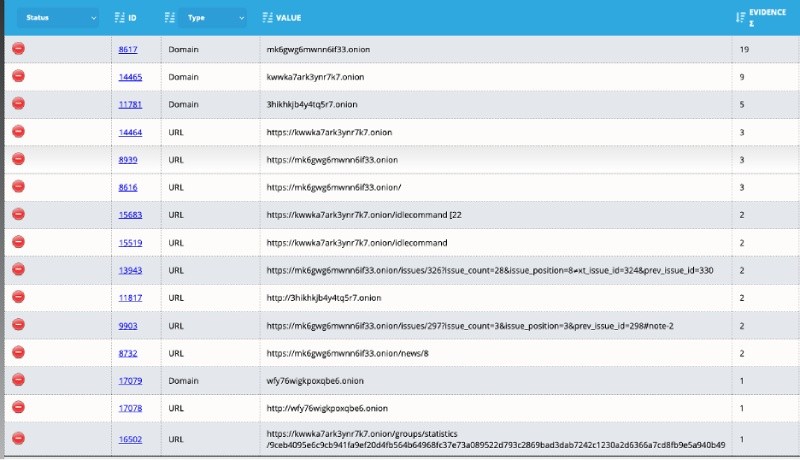
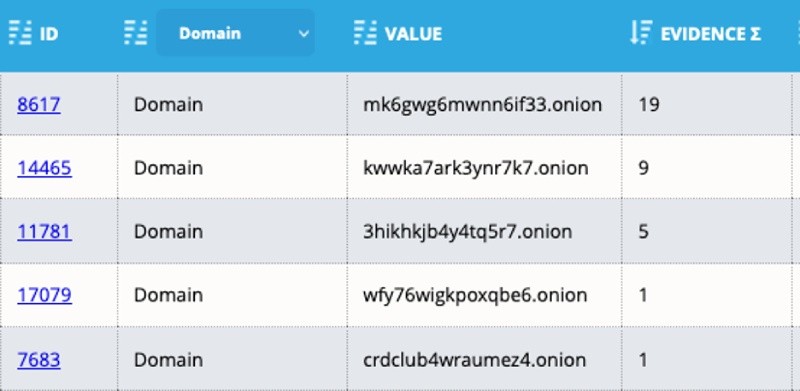
Many of the listed domains/URLs are no longer active, but I could use the evidence section of Analyst1 to quickly read the conversation in which the domain is discussed and gain more insight into its relevance to the attacker.
Wrapping up
As I stated at the beginning of the blog, there is a LOT of data to go through from the leak. While that will take time, as a lone analyst, I gained a lot of information quickly at the start of my investigation simply by extracting the data to the Analyst1 platform and correlating the data within. I had many other findings early on by using Analyst1 to correlate the data and expand on its context by conducting research on each lead. Many of the interesting findings have since been reported by other researchers and security organizations which is why I have not included everything here. However, I thought this use case presented a unique way to use a threat intelligence platform and allowed me to share some of the interesting aspects of my early research from the first few days of the leak. More importantly, I was able to identify previously unknown IOCs seen in Conti attacks and use them to defend against future attacks. In total, I identified:
- 652 domains
- 782 email addresses
- 266 file hashes
- 649 IP addresses
- 4,565 URLs
- 4,323 HTTP Requests
Keep in mind not all of these are from the chat logs alone, but from other Conti data and code released as well. You should also know that many of the IOCs are from websites and services used to facilitate Conti’s operational needs and were not necessarily malicious. For that reason, it takes a human to examine the data and make it actionable, but Analyst1 gave me a head start. Unfortunately, leaks such as this are rare. However, this is the first time we have been able to pull the curtain back and look at a ransomware gang from behind the scenes. Eventually, I may put out an in-depth report on Conti, similar to what I did with a “History of REvil”, but for now, I found the data perfect for this use case and wanted to share some of our own behind the scene details into how I use Analyst1 in my investigations.


